Work From Home Security
Whether you are a small or big enterprise, security considerations are of paramount concern with the sudden changes in working conditions, i.e. a situation where people are teleworking or working from home (WFH). In this short article I’ll give some thoughts on what to consider regarding security for WFH which will be of value for everyone.
To start with, let’s look at the types of enterprise in today’s world of small and medium size enterprises (SMEs):
- Those that host all their services in external cloud and
- Those with some or all of their services held in their network while parts of it is located in the cloud
Security solutions for both types of SMEs will be different, but security issues essentially will be the same. Security issues are associated to assets and any required security solution will depend on implications of the security issue to business or human safety that in turn will lead to security solutions that the given enterprise should use. Instead of going into all these details, let me jump directly into some of the use-cases associated with WFH and considerations for solutions.
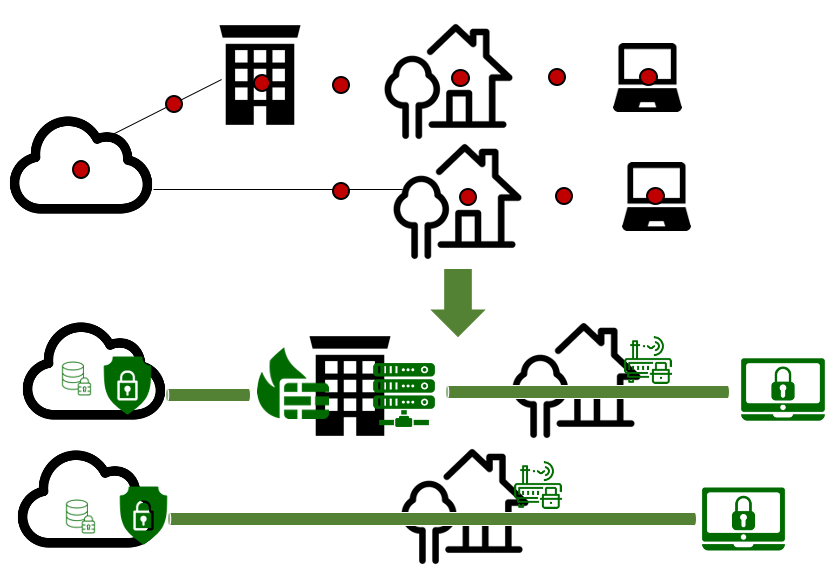
In-case of WFH it is normal that the employee uses a laptop that is connected over WiFi to the enterprise resources over the Internet. The employee will do all office-related tasks such as accessing files, email, browsing but also in addition participate in various other forms to communicate for regular in-office purposes such as social media, web conferencing and various means to chat. All data will be stored on the employee’s device. So what are the associated security:
- Data: Ransomware or data leaks can happen, thus requiring proper data protection considerations for the device is needed. At the end this data is of prime importance for the enterprise.
- Applications: Attackers could enter the device through application weaknesses (including browser, email clients, web conferencing etc.) that could also lead to access to enterprise or personal services of the employee. Hardening and baseline security considerations are called for here, such as updates, strong password and proper settings based on the application in use. In addition security aspects for each application should be considered separately.
Especially proper considerations should be given for email where several issues arise such as account takeover, error in sending files due to lack of attention or phishing attacks. It is also worth noting that as email becomes secure or usage decrease, attackers will move to other commonly used applications (enterprise social media, web conferencing etc.). - Device: A device in this context refers to hardware and operating system (OS). Weaknesses here could lead to similar issues as mentioned in the previous paragraph, but a successful attack on OS or firmware of the device could lead to even worse implications since the attacker will get control of the whole device. Besides the baseline security considerations given in applications, the device should also have appropriate network security and malware protection.
In addition the IT manager should have the possibility to manage the device from remote and have means for security monitoring.
A separate issue is the physical security of the device. A stolen device means all data of the enterprise will be lost potentially giving means to connect to the enterprise network resources as well. This brings the necessity of device bootup security and data encryption in the device. - WiFi and Internet connectivity: Very often the WiFi access point at home is left with defaults username and password even for the management port. Thus, by using WiFi, anyone can perform a targeted attack by finding the location of employees of a given enterprise. An attack will be possible on the device as well as anything associated to the enterprise, since the attacker can have access to the communication channel. This calls for adequate security settings for home WiFi.
Similarly, the traffic between enterprise services and device traverses the Internet, through which or from where any attacker can cause similar attacks as above.
This requires appropriate home network security, including Firewall etc. The device should also have a VPN connection to the enterprise servers or services in the cloud. - Enterprise network, servers and services: The security means mentioned above are obviously of no use if the enterprise network, servers and services – be it in the enterprise office or in the cloud – is not appropriately protected. Several SMEs are not there yet. Attack to enterprise network would mean complete loss of business. Appropriate network security and monitoring solution are thus required.
Although not mentioned above, security awareness and other training are become increasingly essential in current condition. Security trainings that are to the point, practical and engaging are required for all employees. Such trainings by itself will lead to decrease in successful attacks since human factor plays a key role in security. This will also help against issues associated with social engineering (e.g. phone call as a manager requesting information), which has caused serious issues to several enterprise worldwide.
A common point among all the items above is proper identity and access management (IAM) for all aspects and operations & management (O&M). Where IAM for all aspects covers device, network, home network and each employee; including password rules. While, secure remote O&M is a necessity for WFH given that the IT and network administrators are also working from home.
This article is meant to give an overview of potential cybersecurity issues associated with WFH and potential direction for solutions. We hope that the article is beneficial for everyone. Finally, we strongly advised that any enterprise, or anyone, should consult with security experts to ensure a sound security strategy for their remote workforce.
Anand R. Prasad
Dr. Anand R. Prasad is a global leader and expert in information and cyber security who has delivered security solutions for 5G, 4G, virtualization, SOC, Wi-Fi, mobile devices, enterprise and built GRC processes from scratch.
Anand is Founder and CEO of wenovator LLC, a global provider of cybersecurity services and consulting with top-tier clients right across the telecommunications industry. Dr. Prasad is also a Senior Security Advisor of NTT DOCOMO, providing advise on all aspects of cybersecurity for the company, Advisor to CTIF and Advisory to GuardRails. Prior to which he was Chief Information Security Officer of Rakuten Mobile, the world's leading MNO with the very first cloud-native 4G / 5G network implementation. As CISO of Rakuten Mobile Anand led all aspects of enterprise and mobile network security from design, deployment to operations.
With over 20 years of experience, Anand has also held key roles in NEC, Genista, Lucent Technologies and Uniden. He is an innovator with over 50 patents, a recognized keynote speaker (RSA, GWS, MWC, ICT etc.) and a prolific writer with 6 books and over 50 peer reviewed publications. Anand was the Chairman of 3GPP SA3 where he led the standardization of 5G security. He did his ir (MScEE) and PhD from Delft University of Technology, The Netherlands. He is a Fellow of IET, Fellow of IETE and CISSP. Anand is Editor-in-Chief of the Journal of ICT Standardization and Co-Founder & Co-Editor of Cybersecurity Magazine.

