This article is part of our series on Open Source Intelligence (OSINT). Find all articles here.
As the world continues to digitize, the dependence on technology to do business will increase in both the public and private sectors. In today’s information age, organizations use technology to increase productivity, save internal and external operational costs, enhance data security and to expand business capabilities. The main key to achieve these benefits is to implement digital transformation of all work aspects and especially by storing data digitally as a replacement of paper files. Individuals also became very dependent on technology in their daily lives, almost everything people do involves technology in one way or another.
The rapid shift to the digital age was accompanied by a growing increase in cybercrimes. According to cybersecurityventures[1], cybercrime damages will reach $6 trillion annually by 2021. The same study predicts that there will be 6 billion Internet users by 2022 (75% of the projected world population of 8 billion), consequently, the proliferation of digital devices will generate a huge amount of digital data every second.
Digital Forensics (also widely known as computer forensics) is the process of investigating crimes committed using any type of computing device (such as computers, servers, laptops, cell phones, tablets, digital camera, networking devices, Internet of Things (IoT) device or any type of data storage device). Digital forensics is also responsible for examining attacks originated from cyberspace like ransomware, phishing, SQL injunction attacks, distributed denial-of-service (DDoS) attacks, data breach and any sort of cyberattacks that cause financial or reputation loses. The ultimate goal of a digital forensics investigation is to preserve, identify, acquire and document digital evidence to be used in the court of law.
Under this definition, digital forensics is used to investigate any crime that involves using electronic devices, whether these devices were used to commit or as a target of a crime. Having a digital forensics capability becomes very important for modern organizations to investigate internal policy violations and external attacks against their computerized systems, for instance, big corporations already have such capability that exceeds the capability of many government police departments.
Digital Evidence
As I already mentioned, the main task of any digital forensics investigation is to acquire, preserve, examine and present digital evidence to be used in the court of law, so what is meant by the term digital evidence?
Digital evidence (also known as electronic evidence) is any information stored or transmitted in digital format, this includes data found on computers, laptops, cell phones, tablet, PDA hard drives, and all data stored using various storage device media such as USB thumb drive, SD cards, external hard drive, CD/DVD. Data transmitted via computer networks is also considered a part of digital evidence in addition to operating systems and database logs.
Digital evidence should be acquired in a Forensically Sound manner. “Forensically Sound” is a term used by digital forensics examiners to describe the process of acquiring digital evidence while preserving its integrity to be admissible in a court of law.
Digital evidence includes the following artifacts – and more:
- Email messages and attachments
- User account info (username, password, personal picture…etc.) for both online accounts (cloud storage, social media) and local computer accounts.
- Digital photo, audio, and video
- IM conversation history
- Web browsing history
- Files generated by accounting programs
- All types of electronic files (MS Office files, database, spreadsheet, bookmarks…etc.)
- Data in volatile memory (RAM)
- Registry info (in Windows based systems)
- Computer backups
- Networking devices records (router, switch, proxy server, firewall)
- Printer spooler files
- ATM transaction logs
- Fax & copier machines logs
- Electronic door looks log
- GPS track logs
- Digital data extracted from home appliances (smart TV, smart refrigerator)
- Surveillance video recordings
- Encrypted and hidden files
- And any data stored in digital format and can be used in the court of law as evidence.
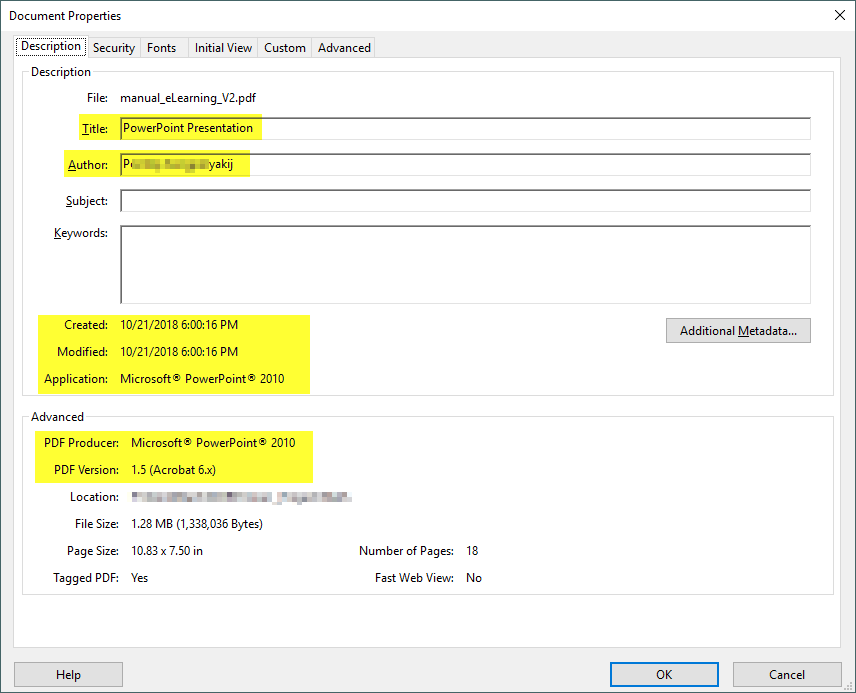
We should take note that most digital file types have associated metadata (see Figure 1), for instance, metadata is data about data, some are automatically generated by the application that created the file (e.g. file creation and alteration date/time, application version info) and other can be set by the user itself (e.g. file’s author name, comments, and email address).
Digital Forensics Process
There are many methodologies or suggested processes for conducting digital forensics investigations, however, they all share the following 4 key main phases (see Figure 2):
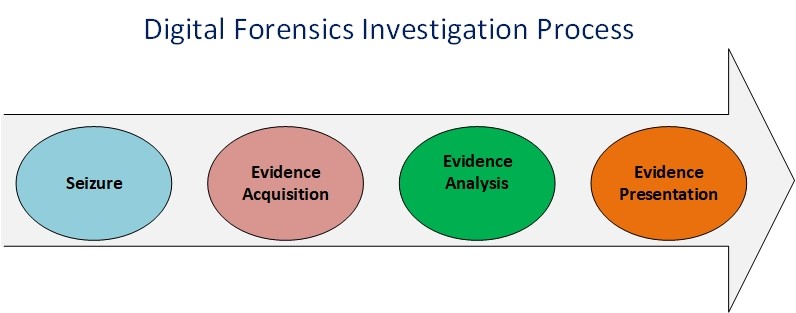
Seizure
In this phase, the suspect digital device is seized and packaged properly and taken to the digital forensics lab. An investigator should have an official search warrant from the court and he/she must have the proper permission to confiscate the suspect device.
The digital device can be any type of computing device such as a desktop computer, server, laptop, tablet, smartphone, external hard drive, USB stick or backup media, Internet of Things (IoT) device.
Upon arriving at the crime scene, if the suspect device was still running, volatile memory should be acquired first (if possible) before powering off the device. Volatile memory can contain important information for the current investigation, such as passwords, IM chat log, internet browsing history, running programs and clipboard contents.
In some cases, jurisdictional challenges may arise and prevent forensic investigators from seizing suspect digital devices. For example, if the crime was committed through the internet and the suspected machine or server was located in another country, how evidence can be acquired in such a case? Having an international search warrant is difficult and time-consuming and may not be applicable in all cases.
Evidence Acquisition
In this phase, a professional computer forensics technician will duplicate suspect device hard drive -and RAM if applicable- to acquire a complete image of it (also known as bit-to-bit image). It is preferable to have more than one forensic image as the examination will be performed on these copies in the lab.
Evidence Analysis
In this phase, the acquired forensic image is analyzed using different tools and techniques to acquire useful lead form it such as: recovering deleted files and emails, discovering hidden data, retrieving IM chat and web browser history. The forensic tool/s used to analyze the forensic image should be accepted by the court of law. Some popular court accepted tools include the following: EnCase (https://www.guidancesoftware.com/encase-forensic), Sleuth Kit (https://www.sleuthkit.org/autopsy), Volatility (https://www.volatilityfoundation.org) for capturing RAM memory and AccessData (https://accessdata.com).
Evidence Presentation
In the final phase, the forensic investigator will produce a comprehensive report that details his/her findings. The language used to write the report should be well understood by non-technical people such as attorneys, judges, and juries.
Digital investigation types
Digital forensic investigations can be categorized into two categories according to who initiated the investigation:
- Public investigations: This includes all criminal cases managed by government law enforcement agencies and are conducted according to country law. This type of investigation follows three main stages: complaint, investigation, prosecution.
- Private investigations: This type of investigation is conducted by corporations to investigate different cases related to computer crime targeting their IT systems such as policy violations, examining wrongful termination, or leaking of enterprise secrets. There are no formal rules that govern such cases, as each organization has its own rules, nevertheless, private investigations should be conducted following the same strict procedures of the public investigations, as private investigations can later move to the court and become official criminal cases.
Digital Forensics Readiness
As more organizations become -almost- fully dependent on technology to run their business, having a sudden standstill caused by an unwanted incident can have catastrophic consequences on their operations. For this reason, strategies like disaster recovery, incident response, and digital forensic investigation should be fully incorporated into the organizations’ operational structure.
Forensics readiness (see Figure 3) of an organization is defined as its ability to collect, preserve, protect and analyze digital evidence in a forensically sound manner whenever an incident took place, this will help it to reduce downtime and properly investigate the criminal case and shift it later to court if necessary. Having a Forensic readiness plan brings many advantages for organizations such as:
- Force employees to avoid violating company policy as they will have the sense that they will get caught easily if they carry out any illegal activity.
- Forensic readiness will increase the organization’s ability to discover cyberattacks against its IT infrastructure before it escalates and become more harmful.
- Reduce costs associated with digital forensics investigations as the organization will already have the plan, procedures, and tools for acquiring and analyzing digital evidence. This will lead to a fast resolution of any criminal case.
- Compliance with government regulations: Having a Forensic readiness plan becomes mandatory in many countries to assure an organization’s ability to acquire digital evidence in forensically sound manner when required by an internal investigation and before moving the case to official courts.
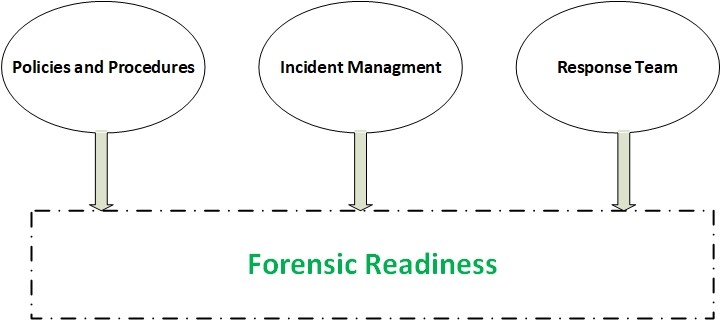
Maintaining a forensic readiness plan has become a must for any organization or corporation that wants to survive in today’s information age.
Conclusion
In this article, I introduced the term “digital forensics” and covered the concept of digital evidence, its types, and where we can find it in electronic devices. There is no standard process for conducting digital forensics investigations; however, I introduced the general phases of any digital investigation process and what tasks are required as a part of each phase.
Digital forensics investigators are needed in all business sectors, most organizations now are maintaining digital forensics readiness policy to meet government regulatory requirements and to better respond to incidents threatening their business continuity.
In the next article, I will remain in the same area and cover how to utilize Open Source Intelligence (OSINT) techniques to support digital forensics investigations to locate information about individuals online.
[1] Cybersecurityventures, “Cybersecurity Ventures Official Annual Cybercrime Report.” https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.



Excellent article
Pingback: Open Source Intelligence - All you need to know - Cyber Protection Magazine