What is Vendor Lock-In and how to avoid it?
The proliferation of digital technologies has impacted how organizations are doing business and interact with customers and vendors. Nowadays, organizations are increasingly utilizing cloud services to facilitate running most of their IT services. Most find that using cloud services is more convenient than building and maintaining their own IT infrastructure. Cloud adoption has accelerated during the rise of the COVID19 pandemic, as most organizations were forced to adopt the work-from-home model to remain in operation during the long lockdown periods.
Cloud services offer numerous benefits for organizations, such as saving the costs of IT equipment purchase and maintainance, increased security, flexibility, mobility, and agility. However, the most important advantage still the ability to scale their operations on-demand, allowing organizations to expand their IT infrastructure to meet the increased workload. The following statistics by Hostingtribunal predicate the increased adoption of cloud services in the near future:
- The public cloud service market is expected to reach $623.3 billion by 2023 worldwide.
- 94% of enterprises already use a cloud service.
- In 2021, the public cloud infrastructure will grow by 35%.
This introduction about cloud computing and its widespread adoption is necessary because vendor lock-in most frequently happens in cloud environments. This article sheds light on the term “vendor lock-in” and discusses best practices to mitigate its negative impact on business operations.
Alluring Aspects of Single Sourcing
The old practice of having one vendor to meet all of an organization’s IT demand in a specific area is still prevalent for many reasons, such as:
- Reduction of compatibility problems between various programs and hardware from different vendors.
- Reduction of procurement time by choosing your services, applications, and hardware devices from one vendor without the need to compare with many other vendors.
- Centralized accountability for any defect or fault in your IT systems, instead of having multiple vendors where each one blames the other when a problem happens, which increases the time needed to solve a problem.
- Streamlined deployment and end-user training, as everything is procured from one company which minimize skills requirements.
- A single vendor Service Level Agreement (SLA) allows clients organizations to cut costs and promise their customers with enhanced service availability and performance. In addition, it promises to provide excellent ongoing support and huge discounts if a customer selects to utilize its IT needs from a single vendor.
Despite the many advantages of having a single vendor, sticking to one vendor in today’s complex IT environment can bring severe problems and can result in significant money losses over time. For instance, suppose having all your IT infrastructure, or business-critical systems, in the hand of one third-party provider. Does such scenario makes you feel rest or fright?
What is Vendor Lock-In?
Vendor lock-in is the situation where an organization becomes over-reliance on a single vendor to provide its IT services without the ability to move to another vendor because of various constraints (e.g., technology, cost, time) that make the shift unfeasible.
Vendor lock-in can happen when using a service (e.g., cloud computing service), software, or a hardware product, and the customer is forced to remain using it despite being ineffective, having low quality, or costing more. This is because switching to another provider is inappropriate and can result in significant losses or work interruptions.
Let us give an example of a vendor lock-in scenario:
Suppose your organization is using proprietary technologies from Microsoft, and you want to move to Amazon cloud service; what is required to do such migration? If you think switching is straightforward, then you are entirely wrong. Consider the data format that needs to be changed between the two vendors; if you have applications and business analytical software at play, how will you reconfigure them to continue operating as usual? What is the amount of time you are going to need to do all this?
Most organizations refer to a service provided by a cloud service provider (CSP), software, or hardware products when talking about vendor lock-in. However, another aspect of vendor lock-in can appear in the cost of training staff on using the new platform. For example, suppose an organization has been with a particular cloud service provider for a long time. Its employees will undoubtedly know how to use its services and configure them quickly because of practice. Now consider the time needed for the same employees to get used to the new platform and user interface if a shift occurs to another CSP.
How to avoid Vendor Lock-In?
Vendor lock-in is considered the main barrier against cloud adoption; this section will suggest best practices that any organization that wants to use a service from a cloud provider must check before signing the contract to avoid falling into a vendor lock-in status.
1. Identify legacy technologies
If your organization uses legacy technologies, then its choice to have a reliable cloud provider is minimal. Furthermore, utilizing a cloud service to run legacy applications can lead to vendor lock-in status, as shifting legacy data and apps into new modern providers can be impossible or too complex in many cases.
2. Examine the vendor exit agreement
Before signing an agreement with your selected cloud provider, check their service terms very carefully, especially regarding migration or moving to another provider. Ensure your future provider facilitates and does not impose restrictions against your shift to another service provider if you want so in the future. Although, for example, many cloud providers set a fee when a client wants to shift its data to another provider, make sure to understand your obligations and the time needed to complete the transfer when needed. This check is necessary, not only if you want to plan your move to another provider but also if your cloud provider gets out of business suddenly for any reason.
3. Compatibility issues
Check your current technology, applications, and data format, and compare it with your future cloud provider offering. If the selected provider cannot offer the required technology that meets your business needs, search for another.
4. Upgrade your applications before migration
Consider checking if your current applications become legacy. For instance, make sure to upgrade all installed applications to discover any problem when moving to a new provider. If all or some of your apps become legacy, your choice of cloud provider will be very limited, leading to vendor lock in the future.
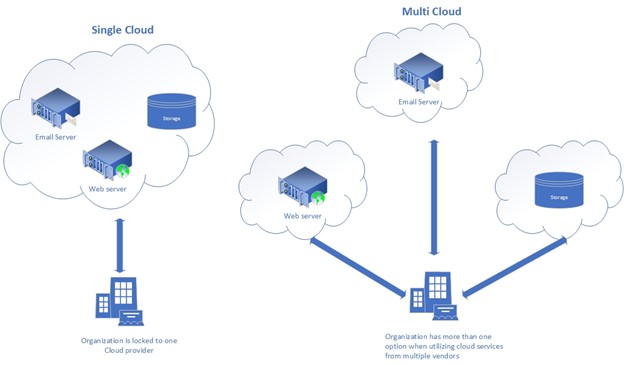
5. Adopt a multi-cloud approach
As we already saw, utilizing cloud services from a single cloud provider has its advantages in terms of compatibility and saving costs. However, using services from multi-cloud providers is the ideal option (see Figure 1).
Utilizing services from multiple cloud providers gives organizations more flexibility to select the best provider that excels in one area. For example, a particular CSP could have great analytical software that meets the business needs of the accounting department. In contrast, another competing CSP has another solution that meets the needs of the Customer Relationship Management department. Utilizing services from many providers help organizations avoid the vendor lock-in problem and select the best provider that excels in a specific work area. However, keep in mind that multi-cloud deployments introduce particular security challenges themselves.
6. Spread the word about the vendor lock-in problem
Makes sure to inform all your organization’s stockholders about the vendor lock-in problem. This issue is not only related to the IT team, as it should see as a general concern that affects all organization departments. Hence, all parties should understand its future consequences and learn about the best methods to avoid it.
Summary
Vendor lock-in has become a significant obstacle in the road to adopting cloud technology on a wide scale. Organizations can mitigate and lower the impact of vendor lock-in by utilizing cloud services from more than one provider. Having a backup of data can also reduce vendor lock-in’s impact if an organization is forced to move to another provider while not performing a smooth shift of its data from the current one.
Dr. Varin Khera
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.

