The Digital Signatures Boom: Email, Document and Code Signing
The Covid-19 pandemic has undoubtedly changed the way we do business, forcing even more of our communications online as face-to-face meetings became impractical. Pivotal to securing these virtual practices is the digital signature.
Although there are many use cases for digital signatures, three of the most common are document, email, and code signing. Securing these three processes is more important than ever in the era of remote working.
With employees working from home, paper-based document signing is no longer viable and instead must be handled virtually. Similarly, staff who used to exchange confidential information in person have transferred these communications to email, with such unprotected messages posing one of the greatest risks for businesses today.
Aware of this uptick in digital business practices, cybercriminals have been developing and distributing malware to steal company information. In turn, enterprises have an increased need to ensure that websites and software downloads don’t aren’t vulnerable to having intellectual property stolen by cybercriminals.
To mitigate the risks of sensitive data being intercepted, organizations are increasingly turning to digital signatures. In fact, the digital signature market has been forecast to reach $14.1 billion in value by 2026, spurred by requirements of the pandemic.
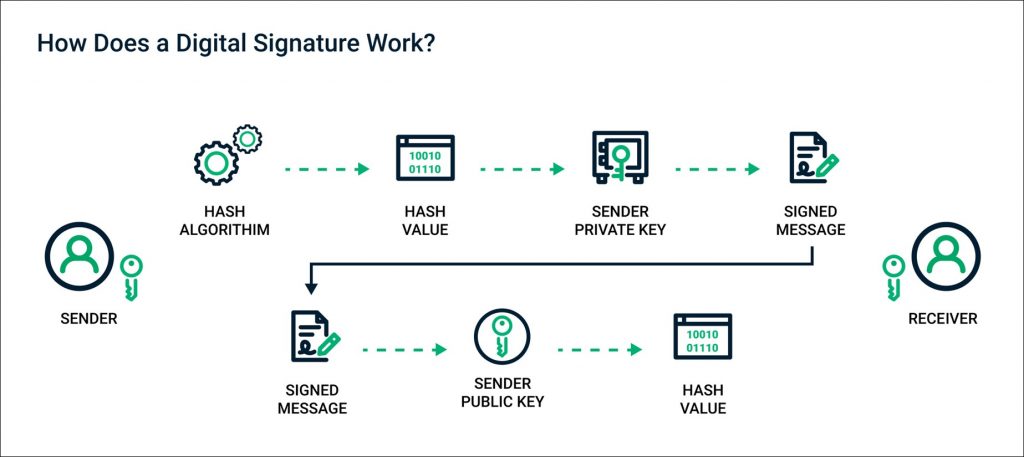
What is a digital signature?
Simply put, a digital signature is a type of electronic seal that leverages public key infrastructure (PKI) to authenticate the identity of the signer. The signature is created by generating a hash, which is encrypted using a sender’s private key. Like a virtual ID card, the signature is then attached to the data, which will confirm to any system that inquires that the data was submitted by the sender.
The signature is uniquely linked to the signer and cannot be recreated or duplicated. Any tampering with the data while it is in transit will be detected, ensuring integrity. The system also maintains an audit log detailing the signing process. Taken together, these factors mean that an author cannot dispute data’s authorship or validity, which is particularly important in contract signing.
There are three common use cases for digital signatures: email, document signing, and code signing. Here are important considerations for each:
Email signing
When seeking a digital certificate solution for emails, there are several things businesses should consider. Ideally, customers should seek the following capabilities:
- Private and public email signature digital certificates
- Centralized encryption key storage capabilities
- End-to-end encryption
- Compatibility with multiple devices, email applications and email gateway services
- Regulatory compliance, for example with the General Data Protection Regulation (GDPR)
- Full certificate lifecycle management
- Crypto agility for supporting new cryptographic technologies
Document signing
Digital signatures are often confused with electronic signatures that could be easily copied and pasted from a PDF or other document without the owner’s consent. However, digital signatures for document signing are based on PKI, and therefore cannot be edited. When it comes to document signing, there’s a few things to look for:
- Compatibility across document types and integration with relevant workflows
- Trusted by Adobe Approved Trusted List (AATL)
- EU qualified certificate issuance
- Authentication methods, including AD, OAuth, SAML 2.0
- Key issuance for portable, cloud or on-premise hardware security modules (HSMs)
- Data protection and residency compliance
- Timestamping
Code signing
As people spend more time online because of the pandemic, malware attacks have increased in frequency. One of the methods employed by hackers involves the use of code signing certificates to make malware appear legitimate, ensuring more people are tricked. This is achieved through compromising the victim’s private key and certificate. As such, it is vital for users to sign their code using a highly secure certificate to prevent this crucial step. When considering code signing solutions, be sure to see if the product includes these important functions:
- EV code signing for high assurance
- Timestamping to ensure signature validity after certificate expiration
- Compatibility in the cloud and on-premise
- Certificate management workflow
Conclusion
Digital signatures are a complex and effective answer to the threats posed by cyberattacks. It is critical to have the right solution in place to protect your organization from every type of digital fraud. As a world-leading provider of digital signature solutions, Sectigo (https://sectigo.com/) provides the solutions needed to reliably safeguard online communications and experiences.
Vinay Purohit
Vinay Purohit is Director of Product Management at Sectigo, a leading provider of automated digital identity management and web security solutions. With more than 20 years of software development and managing cybersecurity products, Vinay leads the company’s innovations around PKI, DevOps, Mobile, and Cloud security. Before Sectigo, he was with Entrust and Nokia Software. He has an Engineering degree in computer science.

