The Security Service Edge (SSE) model provides a convenient, scalable way to make sure users can safely access the Internet, Web, Cloud services, and private company apps anywhere, anytime, whether they are using managed or unmanaged devices. While SSE is a model that is well suited to the way we work today, the shift from on-premise to cloud-based security can result in a significant loss of visibility for security teams. A strategic integration of next generation deep packet inspection (NG DPI) technology in SSE solutions can preserve this vital visibility and the uniform enforcement of global security policies.
Does Experience Have to be Sacrificed for Network Visibility and Control?
In the ”Golden Age of Flying” of the 1950s and ‘60s, carefree travelers enjoyed five-star meals, free-flowing drinks, boundless legroom – and no security screenings! While we all dislike the security lines in modern airports, it’s worth noting that the laissez-faire air travel of the ‘50s and ‘60s gave rise to the less-welcome ’Golden Age of Plane Hijacking,’ which saw 240 hijackings or attempted hijackings—between the US and Cuba alone.
Like the universal physical screening of passengers and bags since the mid-1970s, enterprise IT security managers have for decades run every byte of their network traffic through a central, on-premise data center for thorough vetting. True, there was a performance and user convenience penalty for this set up, but security teams benefitted from 360° visibility into network activities and uniform enforcement of global security policies.
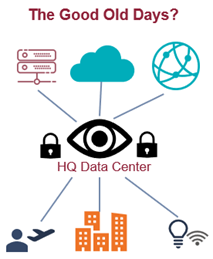
Inevitably though, the hub-and-spoke model of enterprise networking was bound to implode in our BYOD, work from anywhere, SaaS-on-tap world. And with its demise, the ‘Golden Age of One-Stop Security’ is coming to an end. Security professionals understandably worry that bad things will happen as the global visibility and control they’ve long relied on disappears.
Their fears are not unfounded. As the 2021 Verizon Data Breach Investigations Report notes, attacks on cloud assets now outnumber those on on-premise assets, with malicious actors seeking new ways to “take advantage of the natural obfuscation surrounding cloud assets, in which security stakeholders lack the needed visibility and context to understand access and network exposure.”
On the bright side, the cloud also holds the key to regaining visibility and control without sacrificing user experience. One model offering a promising way of achieving this is the Security Service Edge (SSE) framework conceived by Gartner.
What is Security Service Edge (SSE)?
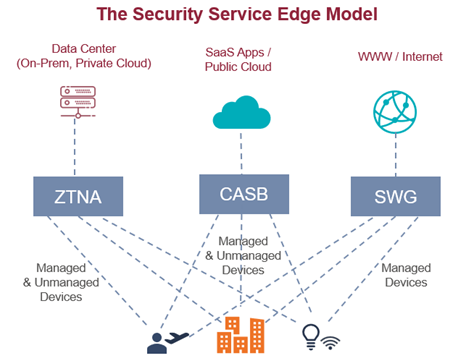
SSE encompasses all the security functions contained in Gartner’s SASE (Secure Access Service Edge (SASE) model, which is a high-level design for integrated WAN and security delivered as a cloud service. While SSE is intended as a framework for a standalone cloud-based security solution which can be deployed alongside an independent SD-WAN solution, it is also used to guide development of security functions within fully unified SASE solutions.
The goal of SSE is to provide a convenient and scalable way to ensure users can safely access the Internet, Web, XaaS services, and private company apps anywhere, anytime, whether they are using managed or unmanaged devices.
SSE solutions accomplish this through three primary components:
- A Secure Web Gateway (SWG) for secure access to the Internet and Web
- A Cloud Access Security Broker (CASB) for secure access to SaaS and cloud apps
- A Zero Trust Network Access (ZTNA) framework for secure access to private apps
Other important components include Data Loss Prevention (DLP), a Next Generation Cloud Firewall (NG CFW), a Web Application Firewall (WAF), and an Intrusion Detection/Prevention System (IDS/IPS). These may be deployed as discrete components or incorporated into an encompassing CASB or SWG.
Scalability and performance are achieved by situating these security functions in edge clouds, and steering traffic to the precise security function(s) required for a given flow. To properly execute this steering and preserve global visibility, accurate application identification is a must, as is the extraction of function-dependent traffic insights.
The natural technology for identifying applications and extracting these insights is Deep Packet Inspection (DPI), which is routinely embedded inside important security components like NGFWs, DLP, and XDR.
The key then to global visibility in SSE is understanding what kinds of traffic insights can be extracted by a DPI engine, which SSE components require which insights, and how DPI technology can be integrated in order to supply traffic intelligence efficiently.
What SSE Functions Can Benefit from Next Gen DPI?
The short answer is every SSE component. At a minimum, each requires an accurate identification of the application in a flow. From there, each function may require additional insights ranging from contextual metadata about a user, device, file, link, action or flow, to advanced anomaly detection.
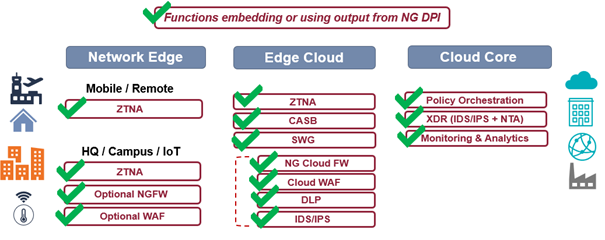
To get the range of traffic intelligence required, commercial-grade next generation DPI (NG DPI) is indispensable, whether it is sourced or developed in-house.
What is NG DPI?
Standard DPI passively analyzes network traffic flows from Layer 2 (data link) to Layer 7 (applications and data) to identify the protocols, applications and services in use, and to extract additional information in the form of metadata to support specific networking and security functions. NG DPI has evolved from standard DPI to meet three additional challenges:
- The rise of encrypted traffic, which impacts the essential visibility required to properly manage and secure networks,
- The emergence of advanced, complex cyberattacks perpetrated by sophisticated criminal actors and nation-states, and
- The shift to cloud-based solutions, with significantly higher performance and scalability requirements.
NG DPI meets these challenges with these distinguishing capabilities:
- Detection of Anomalous & Evasive Traffic
- Advanced First Packet Processing
- Extended Protocol & Application Coverage
- Cloud-Scale Performance
NG DPI Deployment in SSE
After a build or buy decision has been made, the second major step is to determine how to best integrate DPI software, whose output will be used by many components. Typically, the response comes down to an architectural choice between a conventional service chain architecture and a steering model that uses single-pass DPI. Given the unique performance demands of cloud services, the industry trend in SSE is toward the steering model.
Service Chain Architecture
In a conventional service chain architecture, traffic is run through all networking and security functions in a serial fashion, with the same traffic decrypted, processed with DPI, and re-encrypted by each function. However, SSE requires a higher performance model.
Conventional Service Chaining
The Steering Model
The steering model is a higher performing alternative. In this model, upstream encrypted traffic analytics are used to determine if a given flow should be decrypted for in-depth inspection or not, and if so, by which functions (SWG, CASB, IDS/IPS, NGFW, DLP, etc.).
Using NG DPI, it is possible, for example, to identify an encrypted flow as trusted traffic which can be sent on its way without further analysis (e.g., MS Teams audio call), and a flow that requires full DPI processing, decryption and content (payload) analysis (e.g., SharePoint file transfer).
Steering Model with Single-Pass DPI
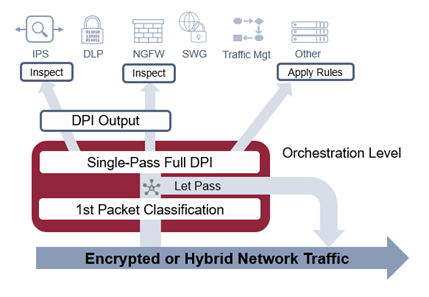
When decryption and full DPI must be used, running DPI once and sharing the results (i.e., single-pass DPI) maximizes SASE performance without impacting security.
NG DPI: The Key to SSE Success
Whether you choose a service chain or steering model, the integration of a high performance, commercial-grade next generation DPI engine is a must for meeting the very specific needs of the converged, cloud-based security environment of SSE. Only NG DPI can deliver vital capabilities like encrypted traffic classification, detection of anomalous and evasive traffic, accurate first packet classification, extended protocol and application coverage (with deep Cloud, SaaS, ICS/SCADA & IoT, and Business application coverage), and cloud-grade scalability and performance.
At a higher level, NG DPI is an indispensable enabler of digital transformation. The IT/OT shift to the Cloud and Internet is essential for support of our evolving ways of working, but it is not sustainable unless global network visibility and the control it enables are preserved for the professionals who develop or manage the security tools that keep us all safe.
Erik Larsson
Erik works with cybersecurity and networking use cases for Enea’s Qosmos DPI and traffic intelligence software. He has an extensive experience from marketing, business development and strategy at high-growth private companies and publicly listed technology vendors.



Leave a Reply