Boosting Suricata with Next Gen Deep Packet Inspection
Intrusion Detection / Intrusion Prevention Systems (IDS/IPS) play an essential role in cybersecurity by detecting and blocking threats that have penetrated endpoint and perimeter defenses.
Open-source Suricata is one of the most widely deployed IDS/IPS, developed and maintained by the Open Information Security Foundation (OISF), a community-run non-profit foundation. It is used by enterprises and public organizations to protect networks, by consultants to provide cybersecurity services, and by vendors who build more comprehensive commercial cybersecurity solutions on top of Suricata.
However, Suricata tends to generate many false positive alerts, has limited protocol and application coverage, and is blind to certain types of advanced threats – especially those using encryption to evade detection. Next Generation Deep Packet Inspection (NG DPI) software can fill these gaps and significantly improve Suricata capabilities.
That’s why leading cybersecurity vendors have started to combine Suricata with NG DPI to enhance products such as Cloud Firewalls (FWaaS), Secure Web Gateways (SWG), Next Generation Firewalls (NGFW), Network Detection and Response (NDR) and Extended Threat Detection and Response (XDR) platforms.
In these products, embedded NG DPI enhances Suricata by:
- Enabling rapid development of whitelists and blacklists that leverage NG DPI’s expanded protocol coverage (particularly for Cloud, SaaS, IoT and OT applications and protocols plus custom and legacy applications)
- Significantly improving Suricata’s ability to detect anomalous and evasive traffic
- Extending Suricata’s ability to detect threats to cover fully encrypted environments
- Significantly reducing the high number of false-positive alerts generated by Suricata through increased network visibility and more accurate traffic identification
- Making threat analysis and forensics faster and easier through high-value contextual metadata (while simultaneously reducing the need for full packet capture)
- Increasing performance by enabling offloading of selected traffic (e.g., video streaming)
Architecture overview
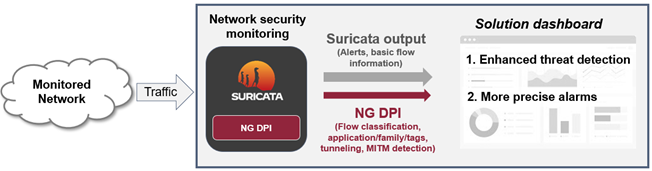
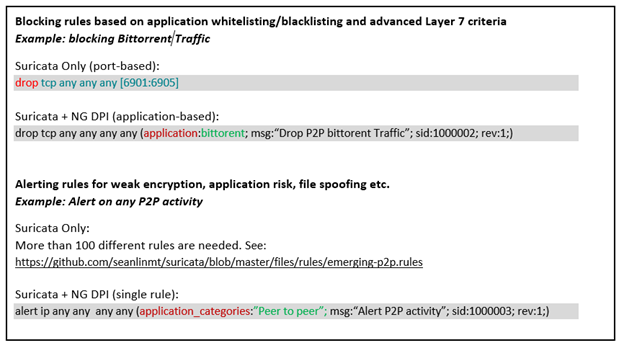
Understanding How NG DPI Can Enhance Suricata Rules
When combined with NG DPI, Suricata rules and alerts are more precise and can be tailored to specific customer environments. At the simplest level, NG DPI’s greatly expanded protocol and application coverage has a huge impact on producing effective rules and alerts. Below, for example, is a look at two rules with and without this expanded protocol coverage.
At a deeper level, NG DPI’s unique security metadata provides valuable insights for rule development, including detection of:
- MITM Interception
- Complex Tunneling
- Anonymizers
- Non-Corp VPNs
- DGA
- Domain Fronting
- File Type Mismatches
- Non-Standard Use of Communication Channels
The last method is a popular tactic for enabling advanced persistent threats, so let’s take a look at how integrated NG DPI improves Suricata’s ability to identify and respond to attacks using this method.
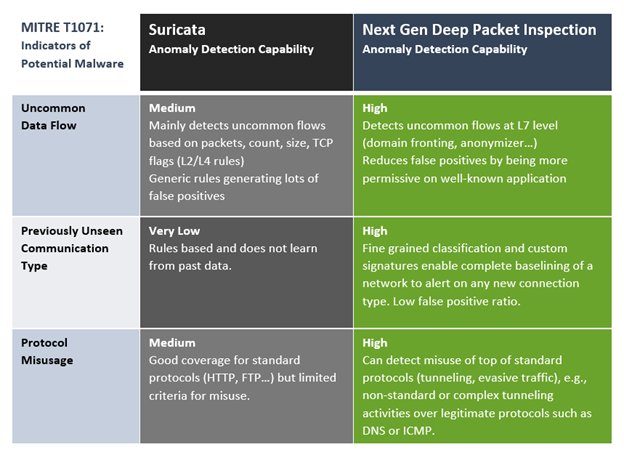
Example of Detecting Command & Control (C2C) Attacks Hiding Behind Common Protocols
To remain under the radar of IDS/IPS systems like Suricata, some C2C attacks encapsulate commands inside common protocols communicating via standard assigned ports. This way, they blend in with normal traffic. This is one of the tactics identified in the MITRE ATT&CK framework of known adversary techniques (Technique ID T1071, Application Layer Protocol). The framework suggests several means of detecting such a covert C2C attack. In each instance, Suricata complemented by NG DPI is far more effective at detecting this type of attack. Specifically, it improves Suricata’s ability to detect and respond to the three indicators of potential malware associated with C2C attacks, as detailed in the chart below.
Summary
NG DPI can add significant value for cybersecurity vendors and operators of critical networks looking to extend and adapt their Suricata IDS/IPS to new network environments and an evolving threat landscape. Integrating NG DPI technology with Suricata improves threat detection, improves alerting and increases overall performance.
Erik Larsson
Erik works with cybersecurity and networking use cases for Enea’s Qosmos DPI and traffic intelligence software. He has an extensive experience from marketing, business development and strategy at high-growth private companies and publicly listed technology vendors.

