Although the zero-trust security model concept was proposed more than ten years ago, the COVID19 pandemic accelerated its adoption since the beginning of the disease in 2020.
Since the start of the COVID19 pandemic, enterprises worldwide adopted the work-from-home model. The massive shift of the workforce to become from home has resulted in an increasing number of cyberattacks. For instance, the traditional network security model that focuses on protecting an enterprise network perimeter to keep the outsiders away from its precious resources becomes useless after allowing employees to access enterprise resources remotely and using their personal computing devices.
In such a complex IT environment where technology changes rapidly, organizations that are still hesitant to adopt the zero-trust model will undoubtedly fall victim to different cyberattacks. For instance, a breach in one part of the network, such as a ransomware infection, will quickly propagate to other areas, leading to full compromise of the organization network and all connected IT systems.
Despite the different security solutions, such as IDS/IPS and firewalls, used to protect networks, recent incidents show many government agencies and private organizations still fall victims to ransomware attacks. Such attacks lead to significant revenue and reputation damage. It was possible because the intruders have only to infect one device within a network to propagate the infection to all connected devices across the network.
This article will introduce the term “zero-trust” security model and suggest best practices to implement this security model to protect against the ever-growing threats of cyber-attacks.
What is Zero-trust networking?
The classical model of network security (see Figure 1) primarily relies on protecting the borders or gateways of the network. To access the protected network, an entity (whether it is a user or system) must provide some form of authentication. Once obtained, the authenticated entity can travel all network locations allocated to it according to a predefined network security policy. This security model could be adequate to protect networks that do not contain sensitive information. However, most organizations these days are storing different types of sensitive data such as customer personally identifiable information, patients records, trade secrets, tax records, and legal documents, to name only a few.
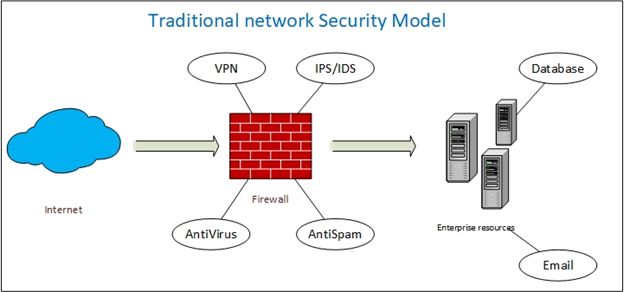
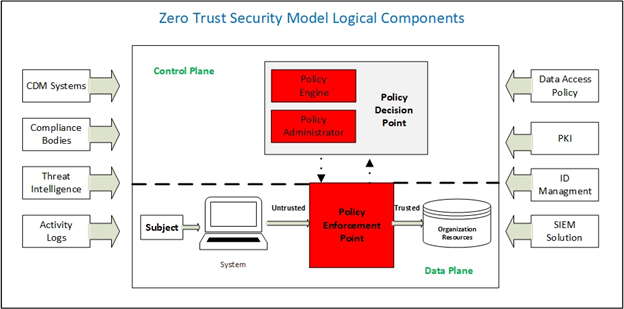
In a zero-trust architecture, things are different. Any entity wishing to access the network will be subject to multiple authentication cycles during its traversal inside the network. As its name implies, zero-trust does not give unlimited access once the entity gets authenticated; instead, it requires “trusted insiders” to authenticate every time they want to access a particular network location or wish to use any of the network associated resources.
To implement the zero-trust model (see Figure 2) in a network, a set of authentication mechanisms, access controls, and validation systems need to be scattered at different points within the network to secure applications, processes, data storage repositories, and other network elements from unauthorized access.
In a nutshell, the zero-trust model means you need to trust no one and must verify everything, even after the subject entity gained authorized access to your network.
Recommendations for adopting zero-trust
It may seem difficult for an organization relying solely on the traditional network security model to turn into a zero-trust model. This section provides some recommendations to facilitate transiting any organization to adopt this highly secure model.
- First, you need to identify the data that you are going to protect. Having a data classification policy is a great start. Data classification will help you discover where your data is located, know who has access to it and measure its sensitivity to your work. Organizations operating in highly regulated environments (e.g., GDPR, HIPPA, and PCI DSS) already know which data is sensitive as a part of their adherence to compliance requirements.
- Draw a map that demonstrates how sensitive data is flowing across your organization network. For example, understand how data flow between applications, understands which data are commonly exchanged between users, which applications are commonly used by users to access/process the sensitive data, and see how other network elements process and use sensitive data. Automated data discovery tools can be used to discover data flow between all elements of your IT infrastructure. Examples of such tools include iotahoe , egnyte and onetrust.
- After knowing how data flows across your network and which applications, network resources, and users are utilizing the sensitive data, begin your work in designing the zero-trust model. You can achieve this by segmenting the networks and installing various access controls, both virtual and physical, to separate different network segments. A network can be segmented according to different criteria. For example, we can separate the segments accessed by remote workers via their devices (e.g., smartphone, tablet, and laptop) from the segments (e.g., data centers) that contain sensitive information and other business-related data. Many organizations are now utilizing the Software-defined networking (SDN) to deploying filtering policies within any area in the network.
- You need to establish security access controls and fill in the filtering policies to deploy them technically across the network segments. Each user must only access the resources necessary to accomplish his/her work, also known as the “least privilege” principle.
- After deploying everything and segmenting your network, you need to monitor network traffic across your IT environment to correct any problem once discovered. All users’ access rights must be continually updated to reflect their roles within the organization. When any employee leaves work, his account must get suspended instantly. Any changes to the requirements of enforced regulatory compliance frameworks must also get reflected when updating your filtering policies and access controls.
Summary
A zero-trust is a technology that helps organizations mitigate data breaches by removing the concept of automatic trust from network architecture. By adopting the zero-trust model, organizations can enhance their ability to fight advanced threats such as ransomware and lateral movement through leveraging micros-network segmentation and multi-layered access controls.
Zero-trust is not only used to enhance data security; it proves helpful to improve your organization’s data management efforts and helps you to have complete visibility over your data flow between your endpoints devices and connected networks.
Dr. Varin Khera
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.



Leave a Reply