Does COVID-19 increase cybercrime?
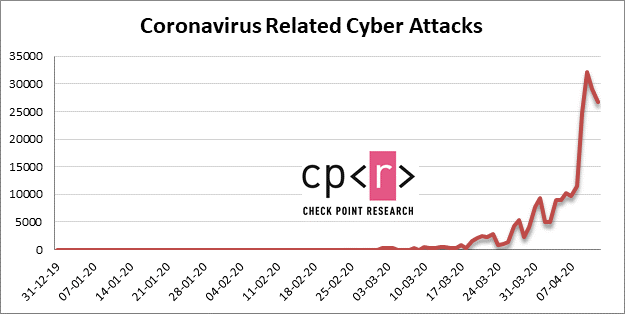
18 million malware and phishing emails daily in connection with the COVID 19 pandemic alone are seen by search engine provider Google with its email service Gmail. In addition, there are more than 240 million COVID-related spam messages per day. Researchers from Check Point have found a variety of domains related to coronavirus-related stimulus or relief packages have been registered globally since January. A total of 4,305 domains relating to new stimulus/relief packages have been registered. In March 2020 – a total of 2081 new domains were registered (38 malicious; 583 suspicious) and in the first week of April – 473 were registered (18 malicious; 73 suspicious). They have also seen a huge increase in the number of attacks, to an average of 14,000 a day, which is six times the average number of daily attacks when compared to the previous two weeks. And over the past week from 7th April, the average number of daily attacks increased sharply to 20,000. The graph in the graphic beneath shows the increase of cyber attacks related to the coronavirus seen by Check Point.
Tim Berghoff, Security Evangelist at G DATA CyberDefense also sees an increase in attacks: “The number of cyberattacks is rising sharply at the moment. This is because cybercriminals attempt to take advantage of the high demand for information on COVID-19. Home users seem to be more affected than companies because the former group spends significantly more time at home now and is therefore online more frequently than usual. GU-Loader is a notable example which is currently active. The malware downloads other malware, such as Agent Tesla or Lokibot. They use links to Google Drive, Onedrive or ufile.io to load the malware. However, older malicious programs such as Trickbot are also very active at the moment. A few large cybercrime groups have announced that they will cease attacks against hospitals for the duration of the crisis. But these seemingly honourable announcements are few and far between and do very little in the way of relief for any companies that are not in the healthcare business”.
The German federal police department, the BKA, has put together a list of typical crime and cybercrime attached to the current hunger for information on the epidemic. Even the WHO itself has put out a warning that cybercriminals are using the situation for their business.
Thales has put together a full analysis of the different attack vectors and found out that the cybercriminal groups are following the virus, while targeting the most affected countries and go to the next once the virus reaches it. The researchers think that the groups that are taking advantage of the situation are the same that have been in business before, but using the new themes to carry out their activities. The timeline beneath shows the spread of COVID-19 related malware as seen by the researchers:

Methods and tactics
To take one example: Users, while at home, get phished by fake maps of the famous John Hopkins University project world map. Security researchers from Qualys have found an example here. They describe a fake map, where a variant of the Azorult malware family has been repurposed to be embedded and run within the Corona Map application. So the information stealing malware, used to steal credential and payment card information in the past is now used again.
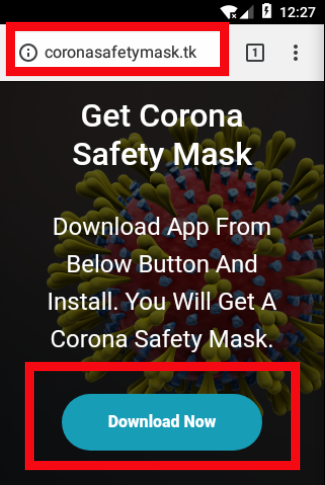
Another example are tricksters who are offering fake masks and other medical items in fake shops. ThreatLabZ researchers from Zscaler recently came across a domain named coronavirusapp[.]site that was serving Android ransomware. The app claims it can notify the user when anyone infected with coronavirus is nearby. Another domain, hxxp://coronasafetymask.tk, asks users to install an APK to receive a “Corona Safety Mask.” The same researchers have noted in the beginning of March, that Corona related scams, back then also related to the Olympic games in Tokio, have been send to a lot of employees.
Researchers from KnowBe4 found an even more scary form of phishing attack. With the increasing infections in the US, the security awareness experts found out that cybercriminals targeted employees working at home with a scary message. “You Are Infected“, was the header of the phishing emails found. The phishing email warns the recipients that they have been exposed to the Coronavirus through personal contact with a “colleague/friend/family member” and directing them to download a – malicious – attachment and proceed immediately to the hospital.
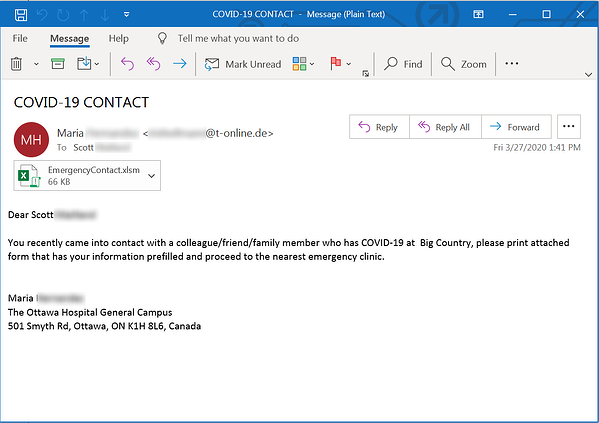
The email is simple, succinct, and alarming. Moreover, it spoofs a hospital, lending additional credibility to this particular social engineering scheme, which is clearly designed to elicit a panicked response from readers and override any form of rational, measured thought.
And this is just the tip of the iceberg, security companies and researchers from all over the world are reporting about new campaigns nearly every day. One example is SentinelLabs who identified a malicious campaign that uses a coronavirus healthcare notification from Canadian authorities to distribute malware aimed at financial institutions.
Conclusion
The initial question was whether there is an increase in cybercrime due to the current crisis? The answer is yes and no at the same time. The numbers of attacks and phishing related to COVID-19 are spectacular indeed, but it is too early to say whether this is more than we’ve seen in the years before. More obvious is, that cybercriminals are taking the hype train and chase the ambulance to jump on it while other business models like crypto mining are no longer lucrative enough. Once the information overkill on the virus also kills the interested reader, the attackers will look for new or the very old ways to infect machines with ransomware attacks to gain their income. This at least is expected by some of the security experts we mentioned above. The more concerning question is how successful these attacks are and how successful they will be, once the home workers return to their offices and spread the malware by synchronizing their work files with the servers.

