Are you aware of the security risks of Network Function Virtualization?
Carrier Service Providers (CSP) around the world are eagerly adopting NFV, leveraging on its versatility and cost-effectiveness to build out their next generation telco capabilities.
What is NFV really and why is it an important domain to discuss from a security perspective? Put simply, NFV is a virtualization of network functions, which in most cases are telco network applications such as mobile gateways, routers, firewall, load balancer… etc., to enable these functions to run as a packaged software programs or virtual network functions (VNFs) on top of commercial-of-the-shelf (COTS) hardware.
In a typical deployment, VNFs sit on top of a virtual machine (VM), which is the virtualized (software) environment emulating a complete system (O/S, Compute, Storage and Network).
From a security standpoint, this deployment opens up a host of new security threats which were not present before when network functions run on proprietary hardware called appliances. With both the network functions and host environment now running on virtualized set up, various vulnerabilities from wrongful access to denial of service to malicious malware become an imminent and real threats.
The point is, adopting NFV as an approach and establishing the infrastructure environment on which it will run on (includes VMs and the NFV infrastructure called NFVI), require a thorough understanding of the security risks associated with this technology.
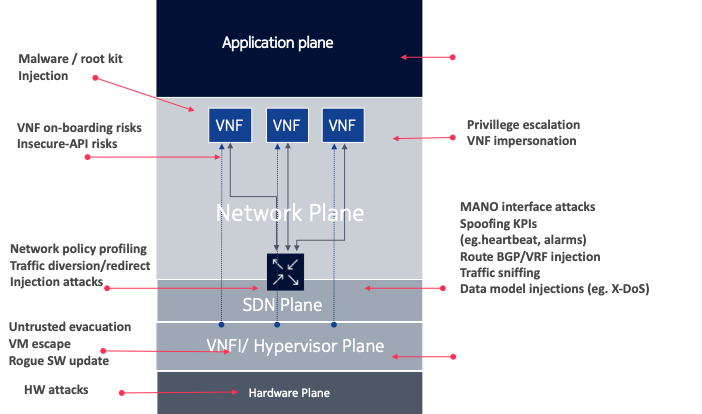
List below are some of the most common types of threats when deploying NFV infrastructure in a practical network.
- Topology risks – In virtual networks, new components can be easily created, this opens doors for poor access control, especially when careful planning is not considered.
- VNF onboarding risks – Poor implementation and onboarding of VNFs can result in inadequate security control being placed on the VNF. This is in contrast to traditional networks, where control is easily seen and visualized.
- Containment risks – Various rootkits exist that have targeted the hypervisor and they are capable of breaching several VNFs simultaneously.
- Insecure API – An attacker can exploit insecure VNF API to dump the records of personal data from the database to the Internet.
- Denial of Service Protection Failure – DoS attacks may be directed to virtual networks or VNF’s public interfaces to exhaust network resources and impact service availability. Similarly, a botnet could infect an insecure VM creating a huge volume of traffic to other VNF.
- Malicious Insider – A malicious administrator can take the memory or screen dump of a user’s VM session. Since the malicious administrator has the root access to the hypervisor, they can, therefore, extract the user ID, passwords, and SSH keys from the memory dump via the search function on the hypervisor.
- Security Logs and Alerting Failure – The attacker can generate a huge number of logs on the hypervisor through bogus activities, making it difficult to analyze logs from other VNFs. An attacker can also delete the log completely to hide his activities making it impossible for any incident monitoring.
In the next blog, we will discuss how to secure NFVI infrastructure using industry best practices and guidelines. For further reading and references please refer to the following document:
Dr. Varin Khera
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.


The article provides a comprehensive insight into the crucial security risks of Network Function Virtualization (NFV) and highlights the importance of proactive measures to safeguard virtualized networks.