5G Mobile Networks are being rolled out throughout the world. We see new industries picking up 5G for their own purposes and bringing in new features and requirements.
Networks have evolved over time, with each generation becoming more open than the previous ones. 4G supported only to a limited degree private industrial or campus networks (vertical). 5G was designed for easy integration of new use cases and to support the networks of those new business partners. The technical and business requirements of new partners drove the industry into embracing cloud technology and other technologies commonly used for web services. In the past, telecommunication networks, to a large degree, used to utilize their own stacks, protocols, and applications, but that has fundamentally changed with the introduction of 5G. While it is now easier for business partners to integrate with mobile networks, it is also now easier for attackers to target said mobile networks.
Not only has the technology of networks evolved, but also how we use mobile networks. It is no longer just about voice calls, messages, and a bit of web surfing. User authentication and authorization are relying on mobile networks and mobile phones to securely enable a wide range of services. Also, mobile networks are increasingly used by IoT devices, on factory floors, in electricity grids, in logistics, in water facilities, in hospitals, and even the military are using 5G. We basically hook up our whole society and daily life into mobile networks. Many private networks will use 5G and their production will critically rely on the security of their communication.
While there have been some known attacks on mobile networks in the past, concerns have been growing that mobile networks might be attacked as part of a larger cyberattack. Political tensions have grown in recent years, especially this year, and cyber is now, for most military, an established division, such as air. Cyber is a fundamental part of warfare.
Clearly mobile networks are critical infrastructures and the importance of protecting this has not been lost on the European Commission. For that reason, the EU´s European Union Agency for Cybersecurity (ENISA) has been investigating mobile network security over the last few years. ENISA has also been given an additional mandate in 2019 through the Cyber Security Act to strengthen and guide member states to improve cyber security.
While the very early stages focused on supply chain risks and risk management, the scope has been extended to general critical communication infrastructure security over time. The importance of security of communication networks has accelerated with COVID19, as many companies have turned to full remote working, and many activities, like contract signing etc, went online. Recent developments in Ukraine highlight the importance of threat sharing and threat intelligence within Europe and associated nations to protect against potential nation state attacks. In February, ENISA and the Computer Emergency Response Team for the EU Institutions, Bodies and Agencies (CERT-EU) started working together on operational co-operation , and knowledge and information sharing.
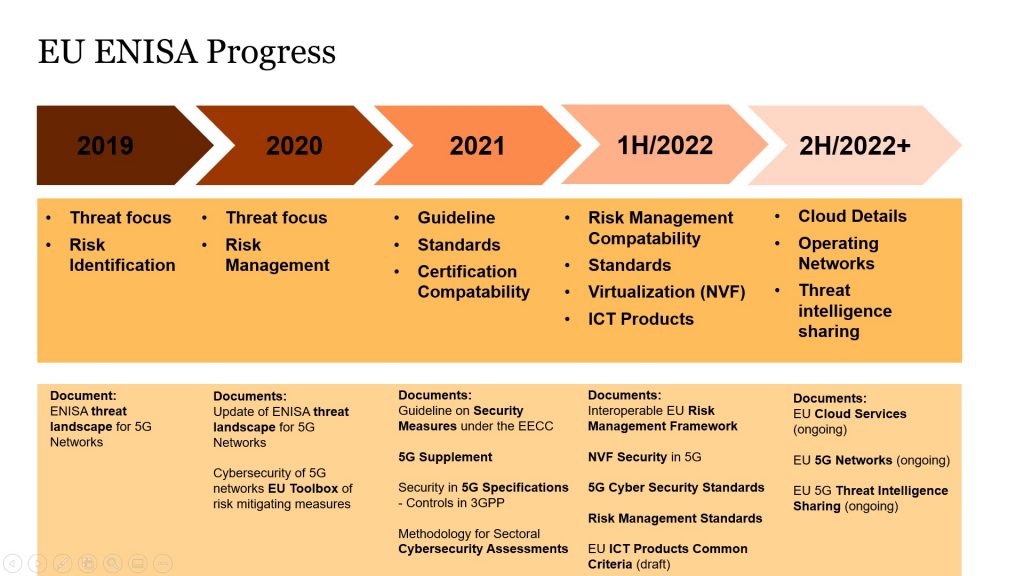
While the line of thought from the EU perspective is clear, the practical implications for mobile operators, cloud providers, and private networks are not so obvious. Mobile operators, verticals, and cloud providers can have a wide range of potential business arrangements.
A mobile operator or a private network (e.g., on a production site) could have one of the following arrangements with a cloud provider. The cloud provider could offer:
- Infrastructure as a Service by providing the needed resources to a mobile operator or private network for OpenRAN and/or core network
- Network Function as a Service by providing the needed core network functions and functional elements for OpenRAN to a mobile operator or private network
- Communication as a Service by taking on the role of an operator and potentially just leasing the frequency from a mobile operator
- Edge Content Cloud by providing an edge content server (as part of a User Plane Function UPF) in a localized cloud
Each of those arrangements has different implications on the responsibility split between cloud providers and mobile operators or private network owners. There are a similar range of possible arrangements between a mobile operator and vertical private network owners. It also makes a difference for the regulatory environment if the communication service is also offered to the general public or just for a specific vertical private network owner.
An additional dimension comes into play through slicing, multinational operators, and Mobile Virtual Network Operators (MVNOs). In those cases, we have different partners inside the network either partially or end to end. The responsibility split for network functions, radio access networks, management and operations, and underlying (cloud) infrastructure needs to be defined.
The decision of the business approach and responsibility split is the first and most important step to understand the impact new EU 5G requirements have. Based on this, each individual requirement must be checked for applicability. Some EU documents have a wide scope such as the EU Guidelines, whereas others, such as ICT product security, have a narrower focus. As an example, the requirements contained in the EU Guideline and the 5G Supplement will apply to all the cloud scenarios above, while the ICT product security will have a key impact on network equipment vendors and ICT device manufacturers.
In the past, regulators and mobile network operators had a cooperative approach. The management of a mobile networks and its security was commonly left fully to the mobile operator without interference or support from the regulator. This is about to change.
The recent UK government draft Telecommunications (Security) Bill introduction is not without severe implications. Ofcom , who is responsible for enforcement of the bill, has stated that the penalty can range up to a maximum of ten percent of the mobile operator’s relevant turnover. While the EU has not yet announced such penalties, we know that the EU has been very serious on data protection and the implications on GPDR. In the current situation, it is prudent to assume that they are also serious about security for communication networks.
Will the EU´s 5G Toolbox have the same impact on mobile communication as GPDR had? The clear answer is: Yes. Therefore, it is time to prepare for the applications of the EU´s requirements on mobile networks, private networks, and the cloud.



Leave a Reply