The number of people using the internet is increasingly growing, with more than one million users accessing the internet for the first time each day. Cybersecurity Ventures predicts there will be 6 billion Internet users by 2022 (75 percent of the projected world population of 8 billion), the usage rate will increase up to 90% of the world population by 2030.
Aside from commerce sales, most internet users are accessing it to socialize and interact with other peers online. For instance, there are 3.80 billion social network users in January 2020, this number has been increasing by about 9 percent since 2019.
The huge transformation from the real world to the digital universe will make most people, enterprises and government interactions happened in cyberspace. The advance of the internet and related communications technology allows easy access to information from anywhere on earth, for example, an online merchant operating in Thailand can offer its services to customers living in the EU and the USA. To handle the spread of personal, financial, medical and other types of personal information across the globe via the internet, the appropriate legal regulations should be settled to protect citizen’s private data and organizations’ digital assets when working online.
Following the implementation of the General Data Protection Regulation (GDPR) in the European Union (which came into force on May 25, 2018), which regulates data protection and privacy in EU countries in addition to the transfer of personal data outside the EU and EEA areas, more countries in the world begin to review and strength their data protection and cybersecurity laws to cope with the new regulation. While the GDPR is an EU regulation, enterprises operating outside EU countries should be aware of its implications to avoid violating any of its terms when dealing or processing personal data of EU citizens.
In this article, I will make a short review of the cybersecurity and Personal Data Protection Acts implemented in major countries in the Asia-Pacific region. Keep in mind that laws concerning cybersecurity and internet privacy are updated regularly because of the ever-changing nature of technology in addition to the development of relevant laws in other jurisdictions and trading partners.
Classifications of Personal information with relation to an individual’s public or private life
We can differentiate between two types of individual’s personal information:
- Personally identifiable information (PII) or sensitive personal information (SPI): This includes any piece of information, which on its own or in combination with other info – uniquely or semi-uniquely – identifies a specific individual. Examples include Full name, birth date, user-name on social media platforms, resume and work history, government-issued identification (passport, driving license and social insurance number), email address, telephone number, mail address, property information, communication records and contents, personal picture, biometric data, credit card number, bank account number and any other factor that can make a person identifiable.
- Anonymous information: This type of info is not strictly related to an individual, hence, we cannot use it solely to distinguish someone online or offline. An example of such information includes Race, national origin, languages spoken, gender identity, blood type, physical traits (height, weight, age, hair color, skin tone, tattoos), income brackets, geographic location (country, GPS coordinates) and online browsing activities such as browsing behavior, links clicked, browsing history.
There was debate whether to consider an internet user IP address constitutes Personally Identifiable Information (PII) or not. To answer this question, I will return to a court decision issued by The European Court of Justice (ECJ) which considers internet users’ IP addresses PII. So, to stay in the safe zone, it is better to consider an IP address PII information, although this rule is not implemented in all jurisdictions around the globe.
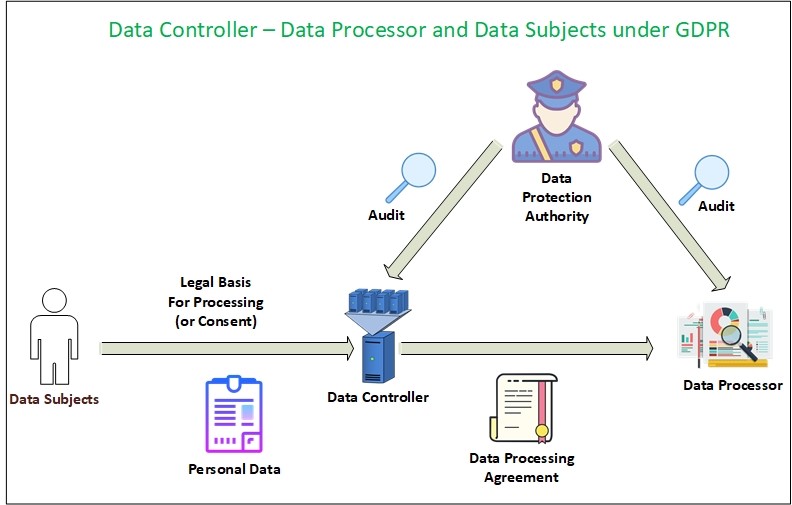
Another thing that we should be aware of as it is generally mentioned in most data protection laws around the world are the concepts of the Data Controller and Data Processor.
Data Controller is the legal entity (individual, public authority, agency, private company) which determines on its own or with a partnership with other entities the purpose of collecting and processing of consumer personal data (consumer is also known as “Data Subject” in most Data Protection laws). The Controller is the entity that directs the activities of the Data Processor.
A Data Processor is the legal entity (individual, public authority, agency, private company) that processes, stores or transmits personal data on behalf of the Data Controller. A Data Processor can only use collected data as instructed by the Data Controller, the Processor is commonly required to keep an audit of all processing activities.
I will give an example to clarify the concept: Most websites use third-party services to serve advertisements and to collect statistical information about their users, for instance when you visit a website (e.g. CNN website) that uses Google Analytics services to analyse visitor’s behaviors, CNN website is considered the Data Controller while Google Analytics is the Data Processor. Another example is when a website uses a provider for email marketing campaigns. The original website visited by the user is the Data Controller while the email marketing provider used to send emails and track users engagement is the Processor.
Data protection laws impose different obligations on Data Controller and Data Processor. For example, under the GDPR law (see Figure 1), the Controller is the main party responsible for consent and governing access to consumer data and is responsible for the lawfulness, fairness, and transparency of information in addition to its responsibility about the confidentiality of personal data. The Controller should select a data processor that complies with the GDPR act.
Now that we know the difference between PII and other anonymous information related to individuals, and can differentiate between a Data Controller and Data Processor, we will begin talking about the main cybersecurity and data protection regulations in the main Asia-Pacific countries.



Leave a Reply