This article originally appeared on riverpublishers.com on 2016-09-20.
Daily, researchers and professionals publish new attacks on IoT products, be it smart homes, factories, wearables or healthcare equipment. Attacks on the IoT results either in surveillance, e.g. monitoring inhabitants in smart homes using the deployed sensors, or exploitation of the physical capabilities of IoT devices, e.g. granting access to a smart home as the experiments on Samsung’s Smart Things prove[1].
Security know-how is broadly available and security experts are trained to understand the impacts of weak information security. They learn methods to prevent vulnerabilities in product design, development, deployment and management. Despite market-related conditions, why are several IoT products still shipped with infancy and few security features today?
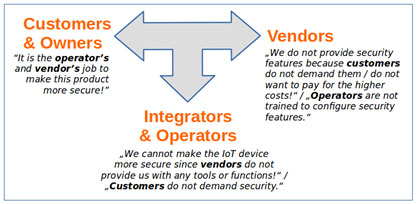
One perspective is an awareness-based role model to describe the dynamics leading to weakly secured IoT products. Caviglione et al. explain a role-based perspective on smart building security [2]. The authors identify vendors, customers and professional operators (typically administrators working with building management systems) as roles with their particular views on the insecurity of smart buildings. According to [3], vendors do not provide security into IT products since customers are unwilling to pay higher costs for it. The vendors’ perspective is cost-centric rather than influenced by high awareness of the importance of securing their products and the long-time implications of selling weakly secured devices on their market position. Caviglione et al. point out that customers lack the necessary security awareness as well and hence, do not demand security features at all. IoT operators, on the other hand, argue that they cannot provide security since vendors do not integrate configurable security features [2].
We extend the view of Caviglione et al. and argue that customers are also pushing the responsibility for lacking security features back to the vendors and so do integrators of products. Customers do not profit from their market-dominating position while vendors show a short-term view on the market situation. Moreover, we observed that the smart building scenario by Caviglione et al. can be extended and that it applies to the whole IoT domain as it suffers from a predominant and persistent dynamic that we call Cycle of Blame: each stakeholder involved in a product life-cycle blames the other stakeholders for the lack of and for not fostering the improvement of security features. An arbitrary number of stakeholders may be involved in this cycle. While large-scale smart buildings require involving professional operators, smart watches do not. Fig. 1 exemplifies a typical Cycle of Blame.
We consider the Cycle of Blame a fundamental process for preventing a higher level of security in the IoT industry.
Whenever progress towards improving security is made, one of the stakeholders is required to take a first step. For instance, vendors were required to make an investment into improved security features while considering to receive no immediate benefit. On the other hand, customers were required to take responsibility for the buying-decisions they make, eventually resulting in denying to buy a product due to the risk of surveillance or attacks. Operators and integrators can be seen as being caught in the middle between customers and vendors. If operators would be aware of their responsibility for the security of the devices they manage, they could deploy one of the existing third-party solutions that shield insecure IoT products. Currently, they do not see their responsibility in considering security criteria in existing systems.
For this reason and due to the discovery of several vulnerabilities in IoT products (cf. [1,4]), we observe that it is crucial that at least one stakeholder in each cycle breaks the Cycle of Blame to foster and accelerate the development and integration of security for the IoT. Online social media should play an extended role in offering platforms for sharing and raising the customers’ knowledge and security awareness. This would result in additional pressure on the operators, who could invest in alternative products, and hence finally put pressure on the vendors to offer secure solutions. In order to safeguard their market share, foreseeing vendors should build an alliance with customers. Based on customer requirements, they may elaborate stringent security criteria to be guaranteed in their products. This would result in pressure on the other vendors to implement security mechanisms and hence, lead to slowly break the Cycle of Blame.
References
[1] E. Fernandes et al.: Security Analysis of Emerging Smart Home Applications, Proc.2016 IEEE Symposium on Security and Privacy (S&P), San Jose, CA, USA, 2016, pp. 636-654.
[2] L. Caviglione et al.: Analysis of Human Awareness of Security and Privacy Threats in Smart Environments, Proc. Human Aspects of Information Security, Privacy and Trust, LNCS 9190, Los Angeles, pp. 165-177, Springer, 2015.
[3] R. Anderson: The economics of information security, Science, Vol. 314, pp. 610-613, 2006.
[4] K. Koscher et al.: Experimental security analysis of a modern automobile. Proc. IEEE Symposium on Security and Privacy, pp. 447-462, IEEE, 2010.



Leave a Reply