Real-Time Vendor Scanning Is Not Optional
One of today’s top cybersecurity search terms is “NIST cybersecurity framework.” The National Institute of Standards and Technology (NIST) framework is so popular because it is easy to understand. It is often used to facilitate technical conversations with business-side stakeholders, which is especially important since cybersecurity is a Board and C-suite issue.
And of course, a trending cybersecurity search term is “SolarWinds.” The megabreach called Sunburst was hidden within SolarWinds’ Orion software update. When its customers updated Orion, they were infected.
Sunburst was a supply chain cyber attack. Companies manage such risks under broad umbrellas such as ERM (enterprise risk management) and information security. The specific programs tasked with preventing and mitigating supply chain cyber attacks are often referred to as vendor risk management (VRM), supply chain risk management, or third-party risk management.
Timing is Everything
NIST’s most recent guidance in December of 2020 emphasizes the importance of real-time monitoring in ERM:
“The severity of a given vulnerability increases exponentially
after it becomes publicly known.”
In other words, speed is essential. NIST and other vulnerability detection groups have the job of immediately alerting enterprises to new cyber threats. Then, VRM teams have the job of immediately responding. This represents a major shift. Not long ago, information security measures such as system pentesting and access control were de rigueur. Now, it’s all about speed, and enterprises just can’t get there without real-time monitoring. Something we have highlighted in the past with a focus on SAP applications.
Vendor Cyber Risk is High
NIST acknowledges the cyber threat posed by supply chain vendors. In April of 2018, they issued Version 1.1 of their Cybersecurity Framework. One of the most significant enhancements was a greatly expanded role for VRM. They also enhance their original 2014 cybersecurity ecosystem concept to include technical and non-technical suppliers.
In the ERM guidance referenced above, NIST provides illustrative SWOT (strengths, weaknesses, threats, opportunities) and Gap Analyses to show how vendors may introduce cyber threats or underperform their security roles.
So, some of the essential cybersecurity questions highlighted by the SolarWinds hack include:
- Do we have real-time vendor scanning? If not, then how do we get it?
- How good is our real-time vendor scanning, and how can we improve it?
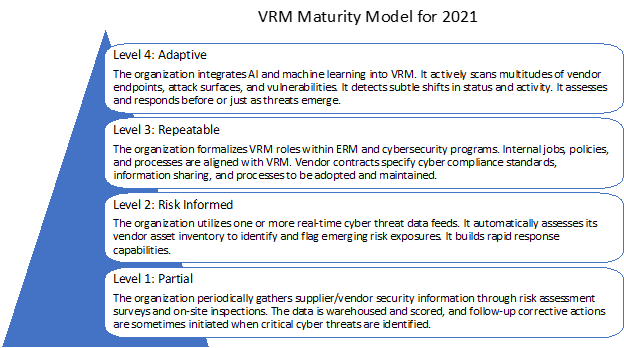
A VRM Maturity Model for 2021
Maturity models have long been used in IT departments to answer questions such as the ones immediately above. NIST refers to Implementation Tiers rather than maturity levels, but the meaning is the same. Their tiers describe increasing degrees of rigor and sophistication in cybersecurity risk management.
NIST uses four tiers: Partial, Risk Informed, Repeatable, and Adaptive. External Participation is defined for each tier, which includes company vendors or technical and non-technical suppliers.
NIST led many organizations to recognize the importance of VRM in cybersecurity. But much has changed since their last version in 2018. The Implementation Tiers need an update, especially given the tremendous threat vector introduced by vendors in the supply chain.
Tier 1: Partial
At the lowest maturity level for VRM, NIST’s definition includes: “The organization does not understand its role in the larger ecosystem with respect to … the cyber supply chain risks of the products and services it provides and that it uses.”
In 2021, enterprises must have a basic understanding of their cyber ecosystem. If a substantially sized company is not paying attention to VRM, they are not a safe business partner. A more appropriate Partial maturity level should read something like this:
The organization periodically gathers supplier/vendor security information through risk assessment surveys and on-site inspections. The data is warehoused and scored, and follow-up corrective actions are sometimes initiated when critical cyber threats are identified.
Companies that conduct periodic risk assessments and on-site inspections understand the basics of vendor cyber risk. They learn to collect vendor cyber risk information, assess it relative to pre-defined evaluation criteria, and determine when to initiate corrective actions.
Tier 2: Risk Informed
The next step in vendor risk management introduces a base level of real-time scanning. In other words, to be fully “risk informed” you need real-time vendor risk sensing. You need to detect what is going on between risk assessment surveys and on-site inspections.
The organization utilizes one or more real-time cyber threat data feeds. It automatically assesses its vendor asset inventory to identify and flag emerging risk exposures. It builds rapid response capabilities.
Tier 3: Repeatable
The major VRM effectiveness gap to address beyond Tier 2 involves structure and codification. VRM is too complex and challenging to rely on good intentions. It spans internal and external organizational boundaries. If VRM effectiveness is to become repeatable and systematic, then roles and procedures need to be formalized.
The organization formalizes VRM roles within ERM and cybersecurity programs. Internal jobs, policies, and processes are aligned with VRM. Vendor contracts specify cyber compliance standards, information sharing, and processes to be adopted and maintained.
At Tier 3, the company creates the management systems required to fully execute real-time VRM across business units and functions, within its overall ERM system, and throughout its supply chain.
Tier 4: Adaptive
Now AI plays a critical role. At Tier 2, the organization might automate their VRM assessment surveys, but it uses fixed rules to identify and assess risk. At Tier 4, companies deploy AI and machine learning to adapt and respond in near-real-time. Now VRM targets emerging threats and those that use new, developing, and sophisticated attack strategies and tactics.
The organization integrates AI and machine learning into VRM. It actively scans multitudes of vendor endpoints, attack surfaces, and vulnerabilities. It detects subtle shifts in status and activity. It assesses and responds before or just as threats emerge.
Many ERM programs already utilize AI to manage information security for company-managed systems, but their VRM programs lag well behind. As enterprises are now painfully aware, the only way to prevent another SolarWinds is to bring VRM up to Tier 4.
Conclusion
A VRM Maturity Model for 2021 is summarized in the graphic below. It builds on the NIST framework but reflects what is required in a post-SolarWinds world where highly sophisticated nation-state actors exploit vendor endpoint vulnerabilities.
CISOs know the importance of VRM and are intensely working on upgrading their maturity levels. This updated model can help them describe their current VRM status and where their organizations need to improve.
A CISO recently said they expect the number of security assessments requested by their customers to increase dramatically in the wake of SolarWinds. These assessments will likely probe how well they manage access to their network and data, whether they have another company’s device on their network, and so on.
Every enterprise, large or small, is a potential target of the increasingly aggressive and sophisticated hackers. The commercial risk is too significant to ignore, and the cost to begin to upgrade their VRM program is not prohibitive.

