Even in 2020, phishing scams are one of the most common ways hackers gain access to sensitive or confidential information. According to Verizon’s Data Breach Investigations Report 2020, 22% of breaches involved phishing, followed by the use of stolen credentials in second place. Phishing remains the most important Social Engeneering technique, being involved in more than 80 percent of breaches that feature a social engineering component.
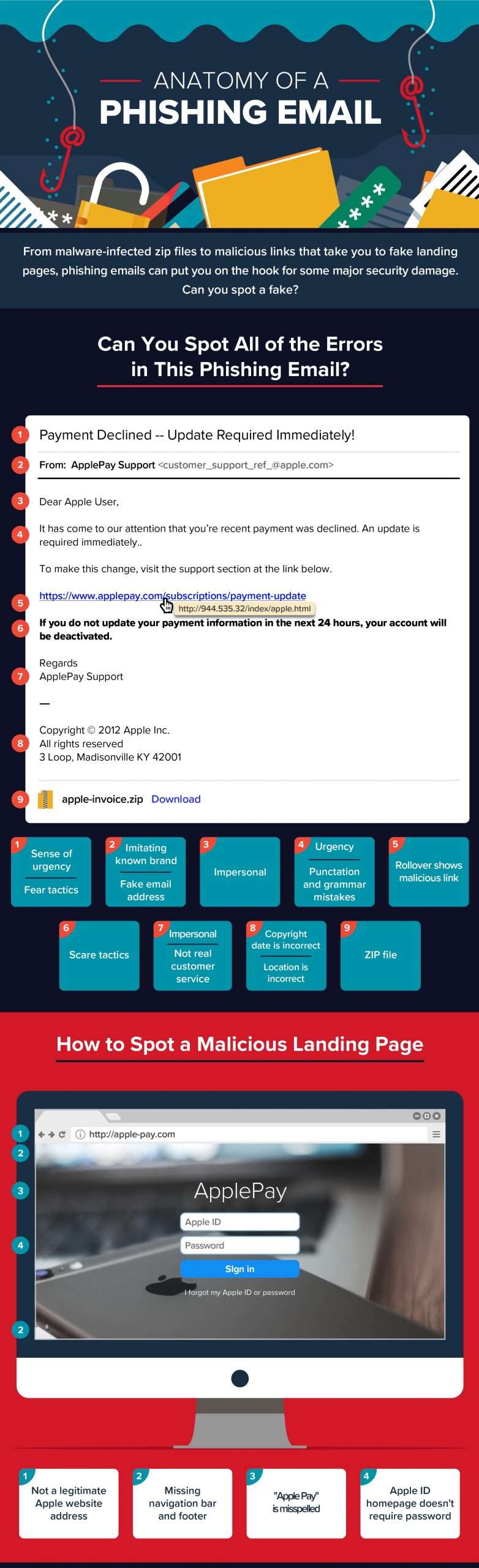
The attackers rely mainly on three points:
Sense of urgency: Phishing campaigns typically aim to create a sense of urgency using intense language and scare tactics, starting with the email’s subject line. Common themes among phishing emails are that something sensitive, such as a credit card number or an account, has been compromised. In the last couple of months, we observed COVID-19 related topics dominating this area. All this is done to induce the recipient into responding quickly, without recognizing the signs of a scam.
Malicious links and attachments: A suspicious link is one of the most important components of a phishing email. These links are often shortened (by bit.ly or a similar service) or formatted to look like a legitimate link that matches the company and message of the fake email. However, if you roll over the link, you will recognize a malicious address that doesn’t take you to the stated web address. If you do click on a phishing link, you will often be taken to a malicious landing page. There are several ways to spot a malicious landing page, like website addresses, which attempt to mimic the web address of a legitimate company, but contain errors and misspellings. In addition to malicious links, phishing scams often include malicious downloadable files, often compressed .zip files, which can infect your computer.
Imitation/fake email addresses: To be “successful”, phishing campaigns must trick the email recipient into believing that the message is from a reputable company. Upon closer look, you can see that both the name of the sender and the sender’s email address is a spoof on a known brand and not a real vendor.
With the increasing prevalence of Emotet, a fourth factor is now added to make identification even more difficult: the hijacking of email threads. Emotet can steal the victims’ email messages and contact lists. The attackers then use the stolen email data to impersonate the sender and “reply” to existing conversations. They can do this either by spoofing the sender or, if they have full control over the victim machine, by sending the email directly from the trusted party. This technique makes Emotet spam appear legitimate and increases the likelihood that a new victim will open a malicious attachment.
As mentioned above, there are several characteristics of a typical phishing email, that can be identified. We have summarized the most important elements in an infographic:



Leave a Reply