I have previously described the importance of having an architecture in place for cyber security. In this article I would like to extend that importance to include having a strategy for the work we do in cyber security.
First, a few pointers on what a security strategy should contain.
A strategy, as well as an architecture, should be based on solid information, such as risk and threat assessments, some of which gets a more detailed treatment elsewhere on this site, which is of critical importance for any security strategy. Without data, we will, at best, create a strategy with no positive effect, at worst we will weaken our defenses. Personally, I like to divide the creation of a strategy up into three levels, starting with a foundation, the actual building of the strategy and an evaluation/updates part, where the strategy gets updated/tuned on a continuing basis to ensure that the strategy remains valid and effective for the organization.
Let’s have a further look at the three levels.
Foundation
The foundation of any work done with cyber security starts with the question, what do I have to protect? Far too often I see companies and organizations that begin security work based on assumptions of what is important. Taking a step back and beginning with a thorough assessment of the infrastructure and using that work as the baseline for any strategy and architecture is a far better option, since it will also help guide decisions on future investments in cyber security. Since we cannot protect everything in our infrastructure 100%, we can use the assessment to assign risks to the various systems and data and use that to prioritize the work and investments in the cybersecurity.
I mentioned risk in the above section. The risk appetite of any company and organization depends on any compliance and regulations that these organizations must live up to, as well as the business areas that they are working in. The security strategy must consider the risk appetite of the organization. Why? Because this appetite will govern how the organization approaches their business area and will depend on the financial strength of the organization at any one point in time. Both of those will be input into the strategy and since both are dynamic, the strategy must be a dynamic entity as well. A quick overview of the risk process can be seen below, it is a flowchart taken from O’Reilly, from the book: The Complete Idiots Guide to Risk management from 2010, an excellent introduction to the risk concept!
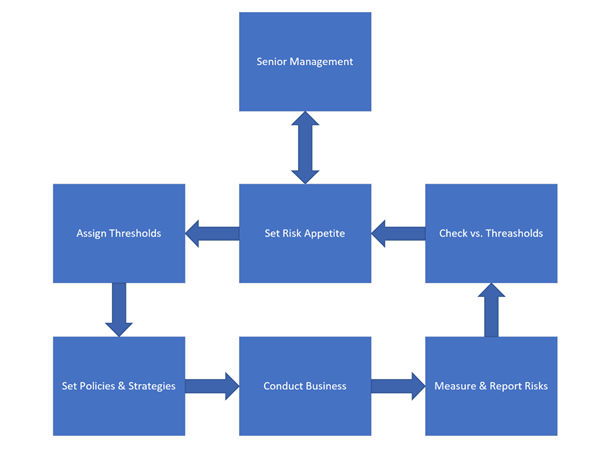
Risks are not risks without threats to materialize the individual risks. Having insights into these threats will make the design and plan for the strategy much more relevant to the situation you are navigating within! A threat assessment will be a very important input into a security strategy but creating a threat assessment is not something that is ‘just done’. It is a very complex and laborious job, which is often plagued by threats that are identified by theoretical implications. The point I am trying to make here is that a threat assessment should be done by people that are trained in this exact discipline, otherwise the threat assessment will become irrelevant for the security strategy!
Building the Strategy
The first step in building the plan is to choose a framework for the basis of the strategy. If you have read other articles by me here, then you are aware of the great respect I have for frameworks, and the time I spend promoting these to customers is significant. Regarding a security strategy, there are a few different ones to consider. The ones I use myself most often are:
- CIS 20
- NIST SP 800-35
- ISO 27001
- COBIT 2019
There are others out there which are just as good as the ones above, these are just the ones I am most familiar with. Which ones to choose is always a challenge but looking at the organization that you are creating the strategy for can help limit the choices to only a few. If the organization is required to maintain high levels of compliance with ISO for instance, then the choice pretty much makes itself. Another way of choosing the framework is to look at the level you are creating the strategy for. CIS 20 is a very operational framework, making it very suitable for operational staff within IT. No matter where the individual staff is focused, databases, servers, networks, and so on, CIS 20 will appeal to their responsibilities. The maturity level of the organization, which I will touch upon next, can also assist in making the right choice of framework. An organization with a low level of maturity will never be a good choice for any ISO framework for instance.
The next step is to evaluate the maturity of the organization. The strategy should help us move the organization from one maturity level to a higher one, hopefully. There is only one framework out there that can assist us in determining the maturity level on the cybersecurity side: CMMC, Cybersecurity Model Maturity Certification. This framework has been developed by the US Department of Defense, based on the CMMI framework. There is a huge push for this framework to become the standard for maturity measurements on the cybersecurity front, ISACA is one of the organizations that are making this push. ISACA is the organization behind COBIT 2019 for instance. If you find a consultant that is CMMI certified, then this consultant can help you with the CMMC evaluation as well.
So, we have a strategy, and we know our maturity level. Now we need to execute on our strategy, right? Well, not quite. We need to think about the business strategy as well when we design our security strategy. The business strategy and the security strategy must go hand in hand in order for our organization to achieve success in both business and cybersecurity! It is here that I most often see a good security strategy flounder, because the staff behind the security strategy does not know about the business strategy or know how to talk to the businesspeople. I have an article elsewhere on this site, with advice on how to communicate with the business as a security professional, using risk as the communication tool.
Evaluate/Update
Like every other thing, cybersecurity is an ongoing process maintaining, executing, and developing a security strategy. If a security strategy is to provide value to your organization, then it needs to be an integral part of the work you do with the infrastructure, policies, and procedures for the organization. Developing the strategy for cybersecurity is the ‘easy’ part of the effort, keeping it on track and relevant, that is the hard part! I usually suggest that the strategy gets a formal treatment on a regular basis, like every 3-6 months, and that there is formal reporting on it to senior management on a regular basis, since it is senior management that controls the business strategy and the security strategy will have to support the business strategy!
I know that this sounds like a difficult job and it can be, depending on how your organization is structured and how it approaches cybersecurity, but just like with security architecture, a security strategy will provide you with a significant boost to the overall security level and maturity. This is something that will become even more important with the new ‘normal’ of remote working and the increased level of regulation that comes from the various governments as response to the increase in data loss we have seen in recent months. Having good cybersecurity will become good business, sooner rather than later!
Tom Madsen
Tom Madsen has been active in the cybersecurity industry for more than 20 years. Tom graduated from the University of Aalborg and covered several technical roles in security during his professional career. He is certified as CISSP, CISA, CISM, CGEIT, CRISK, CCSP, CDSPE and CSSLP, and has published the book “The Art of War for Cybersecurity”. He is currently writing a book ‘Security Architecture – How & Why’.



Leave a Reply