IPv6 Security features – Part 1
This is the first article in a 3-part series, looking into the various security features that are part of the IPv6 protocol stack. The series will follow the below pattern:
- Introducing IPv6 – This article
- IPv6 Security features
- Micro segmentation with IPv6
This first article is a foundation for the next two articles, for those that have not investigated IPv6 before now. If you are a network administrator, with years of experience and daily exposure to IPv6, look out for the next two articles.
The History behind IPv6
The development and history of IPv6 spans several decades. Here is an overview of the key milestones and events in the evolution of IPv6:
- Motivation and Initial Development (Late 1980s – Early 1990s):
- As the Internet gained popularity and the number of connected devices grew, it became evident that IPv4’s 32-bit address space would eventually be exhausted.
- To address this limitation, the Internet Engineering Task Force (IETF) initiated the IP Next Generation (IPng) effort in the early 1990s to develop a successor to IPv4.
- IPv6 Specification Development (Mid-1990s):
- In 1995, the IETF introduced IPv6 as the successor to IPv4, with the publication of RFC 1883, titled “Internet Protocol, Version 6 (IPv6) Specification.”
- IPv6 was designed to overcome the address shortage of IPv4, improve routing efficiency, enhance security, and introduce new features and capabilities.
- Testing and Early Deployment (Late 1990s – Early 2000s):
- IPv6 deployment began with experimental networks and research initiatives. Early adopters and pioneers conducted extensive testing and experimentation to validate the protocol and its features.
- Organizations like the Internet2 project in the United States and the 6bone (IPv6 backbone) helped drive early IPv6 adoption and provided a platform for testing and development.
- Address Space Allocation (Late 1990s – Early 2000s):
- The Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIRs) started allocating IPv6 address blocks to support the gradual deployment of IPv6.
- In 1999, the IETF introduced the “Aggregatable Global Unicast Addresses” format to assign globally unique IPv6 addresses to networks and devices.
- Deployment Challenges and Transition Mechanisms (2000s):
- The transition from IPv4 to IPv6 posed challenges due to the coexistence of both protocols. To facilitate the transition, various mechanisms were developed, such as dual-stack operation, tunneling, and translation.
- Large-scale IPv6 deployments took place in research networks, academic institutions, government agencies, and certain industry sectors. However, widespread adoption in the general internet remained limited.
- Growing Momentum and Industry Support (2010s):
- The exhaustion of available IPv4 addresses, combined with the proliferation of internet-connected devices, increased the urgency for IPv6 adoption.
- Major industry players, including internet service providers (ISPs), network equipment manufacturers, and content providers, started actively supporting IPv6 deployment and promoting its adoption.
- World IPv6 Launch, held on June 6, 2012, was a significant milestone where numerous organizations permanently enabled IPv6 on their networks and services.
- Ongoing Deployment and Maturity (2010s – Present):
- IPv6 deployment has continued to expand globally, with many networks and service providers enabling IPv6 connectivity for their users.
- Major operating systems, including Windows, macOS, Linux, and mobile platforms, have integrated IPv6 support by default, further driving adoption.
- The gradual shift towards IPv6 is ongoing, but IPv4 remains in use due to legacy infrastructure and the need for interoperability between IPv4 and IPv6 networks.
Today IPv6 is a core part of the Internet infrastructure, even if we are still using IPv4 in our own infrastructures. There are no more IPv4 address spaces available for allocation. In cases where we need our own IP addresses, we will have to content ourselves with getting IPv6 addresses.
Introducing IPv6
IPv6 was developed to address the limitations of IPv4, particularly the exhaustion of available IP addresses. It introduces several improvements and enhancements to the addressing scheme and protocol features, ensuring the continued growth and scalability of the Internet.
Some of the key aspects and features of IPv6 are:
- Addressing: IPv6 uses a 128-bit address space, providing a vastly larger pool of unique addresses compared to IPv4’s 32-bit address space. This expansion allows for an almost unlimited number of devices and networks to connect to the Internet directly, without the need for network address translation (NAT).
- Address Format: IPv6 addresses are expressed as eight groups of four hexadecimal digits, separated by colons. For example, a typical IPv6 address looks like “2001:0db8:85a3:0000:0000:8a2e:0370:7334”. To simplify address representation, leading zeros within each group can be omitted, and consecutive groups of zeros can be compressed with a double colon (::) once in an address.
- Autoconfiguration: IPv6 includes built-in support for stateless address autoconfiguration (SLAAC), allowing devices to automatically obtain their IPv6 address and network configuration parameters without relying on DHCP (Dynamic Host Configuration Protocol) servers. This feature simplifies network administration and makes it easier to deploy new devices on a network.
- Larger Payload: IPv6 supports a larger maximum packet size compared to IPv4, allowing for more efficient data transmission. The larger packet size, combined with more efficient header structures, reduces the overhead and fragmentation of packets, improving overall network performance.
- Enhanced Security: IPv6 includes IPsec (Internet Protocol Security) as an integral part of the protocol suite. IPsec provides authentication, integrity, and confidentiality services for IP packets, ensuring secure communication between devices without the need for additional layers of security protocols.
- Multicast: IPv6 incorporates native support for multicast communication, enabling efficient distribution of data to multiple recipients simultaneously. Multicast is integral to many modern Internet applications, such as multimedia streaming and content delivery networks.
- Transition Mechanisms: As IPv6 deployment has been gradual, various transition mechanisms have been developed to facilitate coexistence between IPv4 and IPv6 networks. These mechanisms include dual-stack operation (running IPv4 and IPv6 side by side on devices), tunneling (encapsulating IPv6 packets within IPv4 packets for transmission), and translation (converting IPv6 packets to IPv4 packets and vice versa).
An overview of the IPv6 header can be seen in the figure below.
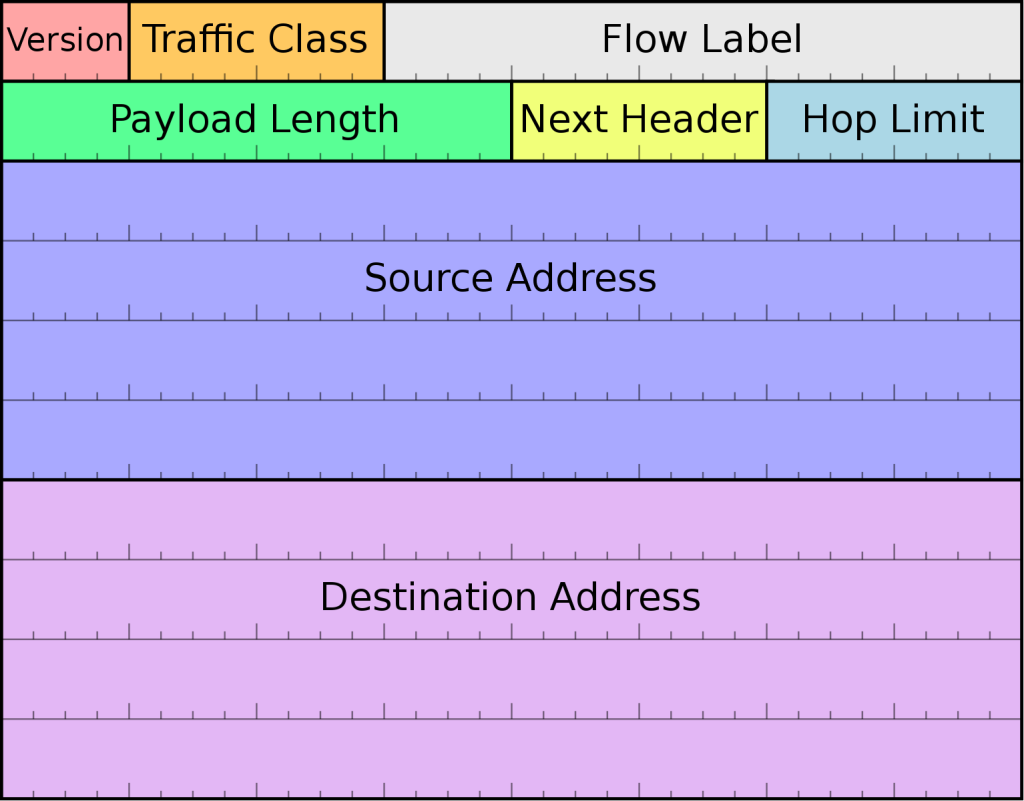
The most prevalent feature of IPv6 is 128-bit address space, giving us 340 trillion trillion trillion individual addresses. This should be enough to tide us over for the next few decades!
New IPv6 protocol features
IPv6 includes several protocols that work together to facilitate communication and provide various functionalities. Here are some important protocols associated with IPv6:
- Neighbor Discovery Protocol (NDP): NDP replaces IPv4’s Address Resolution Protocol (ARP) and Internet Control Message Protocol (ICMP) Router Discovery. NDP performs tasks such as address resolution, neighbor discovery, and duplicate address detection. It enables devices on the same link to identify and communicate with each other.
- Stateless Address Autoconfiguration (SLAAC): SLAAC allows IPv6 hosts to configure their own addresses without relying on a DHCP server. With SLAAC, devices generate their interface identifier based on the network prefix received from routers, allowing for automatic and dynamic address configuration.
- Internet Control Message Protocol version 6 (ICMPv6): ICMPv6 is an integral part of IPv6 and serves various functions, including error reporting, network diagnostics, and neighbor discovery. It provides messages for ICMPv6 Router Solicitation, Router Advertisement, and Neighbor Solicitation, among others.
- Internet Group Management Protocol version 6 (IGMPv6): IGMPv6 is the IPv6 equivalent of IPv4’s IGMP protocol. It enables IPv6 devices to join and leave multicast groups, allowing for efficient distribution of multicast traffic.
- Routing protocols: IPv6 supports various routing protocols, including Routing Information Protocol next generation (RIPng), Open Shortest Path First version 3 (OSPFv3), EIGRPv6 from Cisco, and Border Gateway Protocol version 4 (BGP4+). These protocols enable routers to exchange routing information and determine optimal paths for forwarding IPv6 packets.
- Internet Protocol Security (IPsec): IPsec is an optional security protocol suite integrated into IPv6. It provides authentication, integrity, and confidentiality for IPv6 packets. IPsec can be used to establish secure communication channels between devices, ensuring data privacy and integrity over IPv6 networks.
- Multicast Listener Discovery version 2 (MLDv2): MLDv2 is the IPv6 equivalent of IPv4’s Internet Group Management Protocol (IGMP) version 3. It allows IPv6 routers to discover and manage multicast listeners on a network, facilitating efficient multicast routing.
These protocols, among others, collectively form the IPv6 protocol suite. Each protocol plays a crucial role in enabling the efficient and secure operation of IPv6 networks, supporting features such as autoconfiguration, address resolution, routing, and multicast communication.
IPv6 Address types
IPv6, like IPv4, has different types of addresses to serve various purposes and meet specific requirements. Here are the major types of IPv6 addresses:
- Unicast Addresses: Unicast addresses identify a single interface within an IPv6 network. They allow communication between a source and a specific destination. Unicast addresses can be further classified into the following types:
- Global Unicast Address: These are globally unique addresses that identify individual interfaces on the IPv6 Internet. Global unicast addresses are routable and provide global connectivity.
- Link-Local Address: Link-local addresses are used for communication within a single network link or subnet. They are automatically configured by devices and are not globally routable. Link-local addresses are primarily used for neighbor discovery and network configuration tasks.
- Unique Local Address (ULA): ULAs are used for private addressing within a specific organization or site. They are like IPv4’s private IP addresses (e.g., 192.168.0.0/16). ULAs provide local network connectivity and are not meant to be routed on the global Internet.
- Multicast Addresses: Multicast addresses are used to deliver packets to multiple destinations simultaneously. They enable efficient distribution of data to a group of devices interested in receiving multicast traffic. Multicast addresses start with the prefix ff00::/8.
- Anycast Addresses: Anycast addresses identify a group of interfaces, but the packets sent to an anycast address are delivered to the nearest interface in terms of routing distance. Anycast enables load balancing, redundancy, and efficient service discovery. Multiple interfaces may share the same anycast address.
- IPv4-Mapped IPv6 Address: These addresses facilitate the transition from IPv4 to IPv6. They allow IPv6 hosts and networks to communicate with IPv4-only devices by embedding an IPv4 address within an IPv6 address. IPv4-mapped addresses are represented as ::ffff:IPv4_address/96.
- IPv6 Loopback Address: The loopback address, represented as ::1/128, is similar to IPv4’s loopback address (127.0.0.1). It is used by the host to send packets to itself for testing and diagnostic purposes.
Outro
This was a VERY quick introduction to IPv6 and some of the features involved in the in IPv6. There are of course many more things needed before you are dressed for an IPv6 rollout in your own infrastructures. The multicast features alone, along with the new routing protocols needed for IPv6 are not to be trifled with in a production infrastructure.
There are many books out there describing the IPv6 protocol and providing advice on how to deploy IPv6 in an existing infrastructure. The best one I have read, comes from Cisco press and is called IPv6 Fundamentals, the various configuration examples are of course aimed at Cisco equipment, but if you can look beyond that, the rest of the IPv6 materiel in the book is good knowledge, and it provides enough detail on IPv6 that you can use the book as a basis reference on IPv6.
The next Article in this series will look into the various security features and enhancements that we are getting with IPv6.
Tom Madsen
Tom Madsen has been active in the cybersecurity industry for more than 20 years. Tom graduated from the University of Aalborg and covered several technical roles in security during his professional career. He is certified as CISSP, CISA, CISM, CGEIT, CRISK, CCSP, CDSPE and CSSLP, and has published the book "The Art of War for Cybersecurity". He is currently writing a book 'Security Architecture - How & Why'.

