Cyber Risk Management Scorecard for US Courts
Cybercriminals continue to attack enterprises and federal and state institutions by using sophisticated tools and adopting new breaching methods. Global cyberattacks increased by 32% in 2022, and it is estimated that the cost of cybercrime will grow to US$10.5 trillion by 2025. Within a few months, 4 US courts (Philadelphia[1], Denver[2], Kansas[3], Atlanta[4]) have experienced denial of service cyber attacks to sophisticated foreign ransomware attacks resulting in severe outages for over a month. Cybercriminals threatened to post sensitive court data on the dark web, causing a big disruption in the judicial process. Millions of dollars were paid to Russian state actors as a ransomware to avoid interference in delivering justice at the local and state courts. Because of the ransomware and data theft risks across US courts, the Conference of Chief Justices and the Conference of State Court Administrators have come out with Resolution 2 in support of increased cybersecurity practices in court[5].
Courts with weak cybersecurity practices are at greater risk due to the evolution of malware campaigns, brute force attacks, and vulnerability exploitation. The higher adoption of electronic data exchange by judiciary proceedings after the COVID-19 pandemic has already increased the risk. Therefore, they need a strategic scorecard to proactively safeguard their assets from unforeseen threats. A cyber risk management scorecard tool proposed below will come to their rescue.
Scorecard Methodology
The following 12 categories relevant to courthouse cybersecurity have been assigned a “weighted value” based on criticality, ease of implementation, and overall impact. Each courthouse can revise these categories based on their requirements and technical maturity. The “score” value can vary from 0 to 100. The Courthouse cybersecurity team should assess the score based on the current implementation of each category. The final score (Courthouse Cybersecurity Score) will be determined by multiplying the “Weighted Value (W)” for each category with the score (S) for the respective category and subsequently summing the value for all categories.
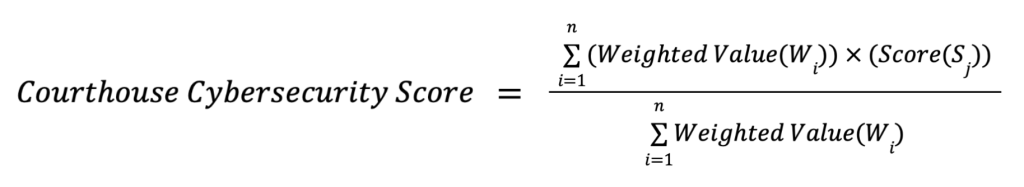
| # | Category | Weighted Value (W) | Score (S) |
| 1 | Cybersecurity data breach in the past 12 months | 10% | 0 – 100 |
| 2 | Violations to industry compliance (HIPAA, PCI, GDPR) | 5% | 0- 100 |
| 3 | Data Retention and backup procedure | 10% | 0 – 100 |
| 4 | Password Management Tool | 5% | 0 – 100 |
| 5 | Disk Encryption | 10% | 0- 100 |
| 6 | Continuous Upgrade and Patching | 10% | 0- 100 |
| 7 | SOC/Monitoring | 10% | 0- 100 |
| 8 | Mean time to detect the breach and recovery (MTTR) | 10% | 0- 100 |
| 9 | % of unmanaged/unknown devices in the network | 10% | 0- 100 |
| 10 | % of known vulnerabilities | 5% | 0- 100 |
| 11 | % of courthouse staff with cybersecurity training | 5% | 0- 100 |
| 12 | % of courthouse devices enrolled in MFA and logging/auditing | 10% | 0- 100 |
Recommendation
- Assign a CISO (Chief Information Security Officer). CISOs are the guardians of the courtroom’s information and data security policy and are accountable for defending it against any potential threats.
- Build a cross-functional team among the courthouse staff: Representation from different teams across the courthouse (Judge, Jury, District Attorney, Public Defenders, Clerk, Marshall etc) will expedite faster implementation of policies.
- Procure cyber insurance: It helps pay for any financial losses they may incur in the event of a cyberattack or data breach.
- Include cyber security Training/Enablement: As Cyberattackers use advanced hacking technology and new attack methods (social phishing, voice phishing, malware, etc.), court staff should continuously learn new ways to be aware of cyber attacks and protect assets. The training must be part of the staff learning day.
- Create and Implement cybersecurity policy: A documented policy for each court (Supreme, Court of Appeals, Superior, State, Juvenile, Probate, Magistrate, and Municipal etc) recommending best practices to protect the assets, including multi-factor authentication (MFA), password rules, mobile device management, data retention, business continuity etc, is extremely critical. CISO must own this policy document.
- Collaborate with third-party security experts: A periodic interaction with third-party independent cybersecurity experts is recommended annually or semi-annually. They can run annual assessments and penetration tests across the courthouse to proactively detect vulnerabilities and provide industry best practices to learn from other agencies and industries.
- Implement a SOC (Security Operation Center): SOC must be enabled for critical courthouses to monitor, respond, and resolve threats 24*7
- Artificial Intelligence (AI) to identify patterns and expedite resolution: Leverage AI models to proactively identify new threats and take corrective actions before damage is caused.
To summarize, there has been an increase in the number of cyber-attacks on the judicial branch at all levels, from the appellate courts to local municipal courts, resulting in many high-profile court disruptions. As the third co-equal branch of government, the judicial branch must protect the integrity of its records and services to preserve the public’s trust and confidence by implementing a risk management scorecard and assessing cyber risks.
References –

Arun Mamgai
Arun Mamgai has more than 18 years of experience in cloud-native application modernization, cybersecurity, open-source secure supply chain, data privacy, AI/machine learning, and digital transformation while working with Fortune 1000 customers across industries. He is responsible for building strategic relationship with technology leaders and promoting Red Hat OpenShift cloud-native application development platform, cybersecurity, and software supply chain solutions.

