You’re under attack and you don’t even know it.
Cyberattacks can happen to anyone; no-one is immune to them. Organizations are especially vulnerable to attacks, including data breaches, with almost 2 billion records leaked in January 2019 alone. Malware attacks were up 200% in 2019, of which this includes ransomware attacks. This means security is a must, not just a recommendation. However, security software such as Network Access Control (NAC), End-point security (EPS) and antivirus software are no longer adequate in protecting against malicious actors. You could be under attack and not one of your security measures would be able to detect it, let alone help you. Why? Rogue devices.
What are they?
Rogue devices are malicious by nature. They are devices that have intentionally been compromised to carry out cyberattacks including data breaches and malware and ransomware attacks. Manipulating a peripheral device with a small computer, such as the BeagleBone Board, allows bad actors to remotely gain access to an organization’s network by creating an out of band connection to bypass an air-gapped network. From here, data can be extracted, or malware/ransomware can be installed without the end-user knowing, causing organizations to be vulnerable to both exfiltration and injection. Often, rogue devices help attackers perform man in the middle (MiTM) attacks, whereby the device intercepts the message from the victim to the entity. The consequences are impactful, and these attacks can even allow attackers to bypass biometric authentication.
Almost 2 billion records were leaked in January 2019 alone.
It is because they look like regular everyday devices that they are not regarded as suspicious by users and, as such, not further investigated. These hardware attacks are impossible to detect by security software solutions as they occur on the Physical Layer, which security software products do not cover. Instead, they are recognized as human interface devices (HIDs), thereby not raising alarms. Once used, these devices can perform keystrokes to disseminate malware onto the endpoint or network, or simply provide the attacker with access to sensitive information which can then be exfiltrated. Either way, the consequences are perilous.
How do they enter your organization?
Target locations
Attackers are smart and they use various means to infiltrate rogue devices inside a company. The free USB iPhone chargers that were being given away at the coffee shop near your office? They have been compromised and were purposely dispensed there, knowing that an employee from the target organization would eventually pick one up and use it in the office. These devices, sometimes known as USBNinja Cables, look exactly like a regular iPhone charger, but they have been manipulated with a small computer inside, such as a Raspberry Pi Zero W. When used by the victim, the device can give the attacker remote access to the network due to its keyboard emulation. Other devices, such as a keyboard or a mouse can also be manipulated this way.
Supply chains
Supply chains are a large risk to organizations due to the numerous amount of third parties gaining access to their sensitive information. The larger the supply chain, the less control there is over how that information is secured. Supply chains provide attackers with multiple points of entry whereby a device can be compromised. This method of infiltration is very real and very threatening, with malicious actors being able to penetrate over 30 companies using rogue devices in the supply chain.
Insiders
Insiders, however, are deemed to be the biggest risk to companies. This is because of the number of ways in which employees can unintentionally cause a data breach, in addition to those who act with malicious intent. 5% of all cybersecurity attacks were intentionally carried out by internal staff. However, attacks caused by unintentional employees pose a higher threat. Crucially, careless/uninformed staff cause around 25% of all cybersecurity attacks, according to a 2017 Kaspersky report.
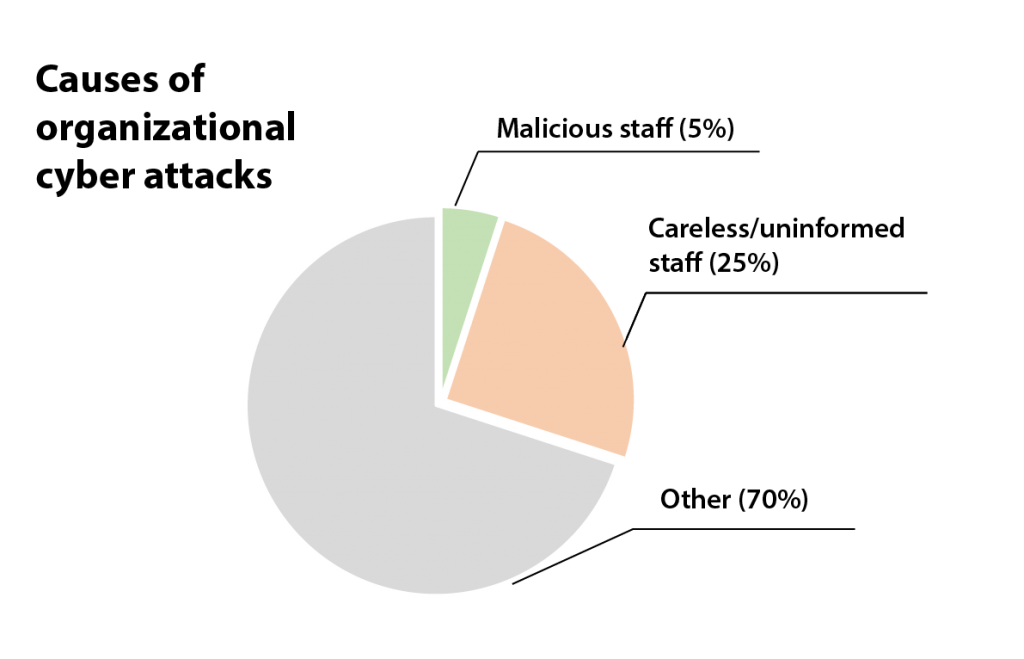
Staff that lack knowledge about the risks surrounding hardware attacks will be less suspicious when using devices, thereby increasing the possibility of rogue devices being used. Moreover, attackers use insiders to carry out social engineering tactics to aid the attack. Threats or blackmail can cause insiders to unwillingly bring, and use, malicious devices in the organization. Alternatively, by manipulating employees to believe they are a colleague, perpetrators themselves can gain access to the premises and deploy their devices.
BYOD and IOT
Employees that use their personal devices for work-related purposes cause organizations to be more vulnerable to attacks. Bring Your Own Device (BYOD) policies, which are being increasingly accepted by organizations, are leading to greater cybersecurity risks. Half of the companies that have implemented BYOD policies have been breached by an employee-owned device. These devices can contain significant amounts of data, making them a prime target for attackers. Charging mobile phones, which have also been used for work-related purposes, at free charging kiosks, for example, can be extremely risky since it is here that attackers can carry out juice-jacking attacks. This is when a free charger has a been manipulated with a small computer that allows the perpetrator to gain access to the endpoint it is plugged into.
Likewise, the rise of Internet of Things (IoT) devices being used for daily activities increases the number of endpoints connected to an organization’s network, thereby raising the risk of a cyberattack.
Consequences
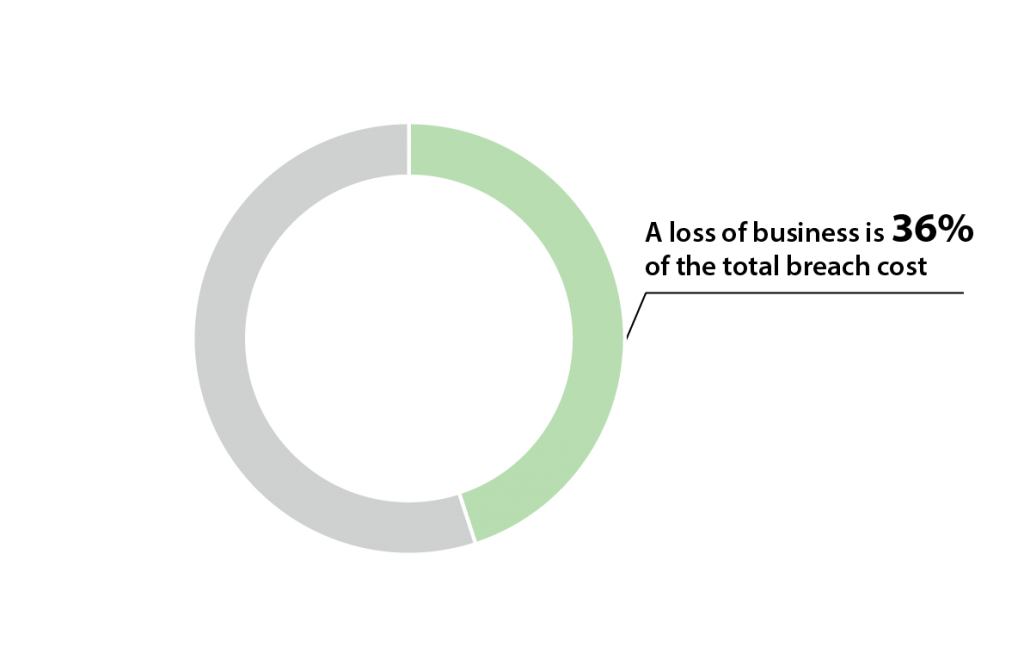
The greatest consequence of these attacks on organizations is financial losses, including direct and indirect costs. The main aim of a hardware attack is a data breach, whereby the rogue device copies and steals sensitive information. Malicious attacks, of which rogue device attacks always are, cost 25% more to resolve than breaches caused by technical or human error. In 2019, the average cost of a data breach was almost $4 million. Worse, the financial loss is felt for years, with, on average, only 67% of the cost being accrued in the first year after the breach. These costs are made up of employee time spent on recovery, negative impact on reputation and, in turn, a loss of business. The latter is the biggest cost to the majority of businesses, causing 36% of their total breach cost, in addition to the reputational loss being onerous to recover from, making it long-lasting and impactful.
Rogue devices can perform keystrokes to download and infect the endpoint with ransomware, whereby the organization will be prevented from accessing their system or files until a payment, usually in the form of bitcoin, is made. Ransomware encrypts the files in question, and only the payment will result in the handover of a decryption key. In Q3 of 2019, the average ransom payment was just over $41,000. Paying the ransom does not, however, ensure that the files will be recovered. The average downtime a ransomware attack caused in Q3 of 2019 was just over 12 days, resulting in a loss of productivity and, in turn, a fiscal loss. Although companies can refuse to pay the ransom and resort to alternative methods of response, there is a risk of not recovering the encrypted files.
Additionally, there can be legal consequences following a data breach which, besides also costing the company money in the forms of regulatory fines and settlement payments, can prevent the organization from carrying out certain operations. This result is especially likely when the data stolen is highly confidential.
Summary
As bad actors are finding increasingly innovative ways to attack organizations, there is an increased threat of hardware attacks being performed. With security software products not developing as quickly as attacking methods, organizations are not protected on the Physical Layer. As such, it will be beneficial to employ an adequate solution to detect and mitigate this form of cyberattack. The consequences of not doing so should be a price too great to pay.
Jessica Amado
Jessica holds an MA in Politics specializing in counter terrorism and homeland security after completing her BA at Regents University in London.

