The year 2020 has broken all records regarding the number of data breaches and other cyberattacks that targeted all organization types and sizes, from governments to enterprises.
As we progress in 2021, cyberattacks continue to escalate in both sophistication and number. And tragically, whether intentional or not, these incidents also affect critical services such as hospitals and other healthcare facilities.
Why do cybercriminals target healthcare facilities?
Healthcare organizations are no exception to cyberattacks. Indeed, many threat actors, especially those backed by nation-states actors and organized criminal groups, find healthcare facilities a lucrative target for many reasons:
- Healthcare organizations are more willing to pay the ransom quickly because of the sensitivity of their work. Losing access to stored data can result in ceasing health care services to patients.
- Patients’ medical records have high monetary value and can sell for a high price in darknet marketplaces. Examples of patient data include Patient Health Information (PHI), financial information such as patients’ credit cards and bank info, Personally Identifiable Information (PII) of patients, and other sensitive information, such as medical research and new medicine ingredients.
- Healthcare providers have adopted digital transformation quickly, therefore their IT systems have suffered from various security holes and unclosed vulnerabilities, making them easy targets for criminal groups.
The great importance of healthcare data makes a data breach a considerable loss compared with other data breaches for other industries. For example, a typical data breach for non-healthcare organizations will cost about $158 per stolen record. For healthcare organizations, the cost per stolen record rises to $355.
Cybersecurity should not be considered a purely technical problem; healthcare providers should integrate cybersecurity into their operational strategy and foster best security practices across all departments. Cybersecurity should be a top priority as ceasing IT systems and other critical health devices can have catastrophic consequences on patients’ lives.
Laws concerning the privacy of patients’ health information
The most noticeable law concerning protecting patients’ health information (PHI) is the USA’s Health Insurance Portability and Accountability Act of 1996. This law enforces establishing national standards to protect patients’ electronic health information created or used by any healthcare entity (including private clinics). To comply with the HIPAA act, principal organizations must apply specific administrative and technical measures to protect PHI and strictly regulate access to such data by authorized users. The HIPAA act was expanded later to include the necessity to report ransomware attacks, even though the attack has not revealed PHI records.
Failing to comply with the HIPAA rules can make the principal organization subject to financial fines and lawsuits from affected individuals. For example, the penalties could reach to $50,000 per violation. Other penalties are determined based on many criteria, such as the number of non-compliance areas and the severity of the incident.
How to protect PHI?
The cyber defense techniques used in other industries are also used to protect healthcare facilities. However, due to the high impact of data breaches in healthcare organizations, especially strong security measures must be enforced to protect PHI.
Use encryption
Patient information and other sensitive medical data must be protected using encryption, in rest, while processing, and in transit. The Internet of Things (IoT) poses a significant security problem in the healthcare sector. For instance, 98% of all IoT device traffic is unencrypted, which leaves the door open for malicious actors to intercept the traffic and capture patients PII and PHI.
Install security solutions
Antivirus and antimalware must be installed on all medical organization computing devices, including servers, endpoints, and network gateways. In addition, it is necessary to install firewalls on all devices connected to the internet and use advanced solutions (like Network Detection and Response) to stop advanced cyberattacks such as lateral movement and APT attacks that typical security solutions cannot detect. Finally, since not all IoT devices are compatible with Antivirus agents, a network-based malware and anomaly protection solution should also be deployed at the perimeter to protect the IoT devices holistically.
Apply software updates
All installed programs and operating systems must remain up to date to avoid leaving an open door for threat actors to conduct their malicious activities. Healthcare providers should promptly apply security patches without delay, and all installed operating systems must be configured to update automatically.
Another critical security problem that most healthcare providers suffer from is the outdated programs used on legacy medical equipment. A recent study found that 83% of medical imaging devices run on operating systems that are so old they no longer receive any software updates at all (e.g., Windows XP and Windows 7).
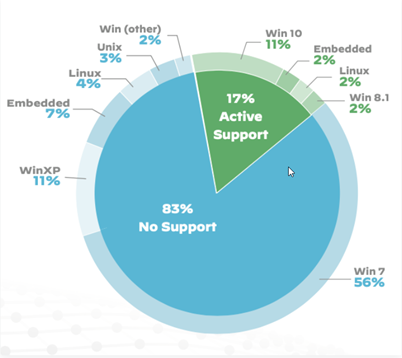
Breakdown of OS support for medical imaging devices – Source: https://unit42.paloaltonetworks.com/iot-threat-report-2020
Integrate security best practices when developing healthcare applications
Following secure coding practices when creating healthcare applications or developing programs for medical devices, including mobile medical devices, is critical to avoid leaving security vulnerabilities that malicious actors can exploit to steal patient information.
Secure mobile devices
Medical mobile devices have become a critical component in healthcare infrastructure. Their widespread usage encourages healthcare providers to develop specialized medical applications to run on patients’ personal computing devices such as smartphones, tablets, and laptops. For medical staff, mobile devices facilities collaborations. For patients, it allows medical staff to provide remote medical support and other assistance, which results in increasing patient stratifications loyalty.
Securing mobile medical devices is as important as securing devices in the immediate work environment.
Have an Identity and Access Management system (IAM)
IAM is a solution for protecting users credentials. It enables access to network services and other resources securely. IAM solutions play two key roles in protecting digital assets:
- Storing users’ credentials (password, access keys, biometric authentication info, temporary security credentials) in a secure, centralized location. IAM creates update and maintain user credentials and help IT administrators to enforce good password security policies such as changing a password once every three months and creating a complex password.
- Regulating users’ access to sensitive resources. This is also known as authorization. The IAM solution will keep track of each user access permission. A secretary, for example, does not need access to a patient’s history of illness.
Create strong passwords
Medical staff should create a strong password to secure their work email and work account. The password must contain at least 20 characters (upper- and lower-case letters, numbers, and symbols) for the password to be considered strong. The password must be stored in a secure encrypted location, such as password managers. If the healthcare organization uses the IAM solution, it will be used to keep staff credentials. Otherwise, other options are available such as:
- A password manager for business
- A third-party Identity and access management as a service (IAMaaS) provider
Enforce Two-Factor and Multi-Factor authentication wherever possible
Protecting access to critical medical systems and other information systems holding patients’ PII is very important. Medical staff must use 2FA to access protected resources, such as passwords and one-time passwords (OTP) sent via email or SMS. Other options include using a person’s biometric information (e.g., Iris scan, fingerprint) in addition to a traditional password.
Backup
Back up systems and data continually. Health information is critical for patients’ lives. In case a successful ransomware attack hits your organization, having a current backup is the only reliable solution to restore operations quickly and safely with minimal disruption.
End-user cybersecurity training
Technical controls are critical to secure protected digital resources; however, without proper end-user security training, your organization is still subject to various cyberattacks despite all your deployed security solutions. Social engineering attacks are still the most significant threat facing healthcare providers. They are considered the preferable entry point used by hackers to gain an entry point to evade security solutions. According to Verizon “2021 Data Breach Investigations Report (DBIR)“, social engineering attacks are responsible for 93% of successful data breaches.
All medical staff within the healthcare facility is responsible for protecting patient’s data. Hence, the issue of data security and patient privacy should be emphasized across all departments.
Summary
To leverage the tremendous benefits digital technologies provide for the healthcare sector, organizations need to deploy the latest security solutions and train their staff about possible cyberattacks techniques and the best methods to mitigate them. Collecting patients’ information and processing it using IT systems is a great aid to improve the overall patient service but keeping this information secure is the most important thing to consider.
Dr. Varin Khera
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.
Amit Gaur
Amit is a seasoned professional with twenty years of multi-faceted global experience; expertise in telecommunications, banking, and IT industries. Amit handled various technical leadership positions and travelled across the world to provide consultancy for strengthening the cybersecurity posture of multiple large organisations.
Amit is associated with Nokia for six years and worked as Head of Security – Global Sales Support in his previous assignment and now working as Principal Cyber Security advisor for APJ Market. Amit has worked with leading organisations and led the execution of strategic initiatives in security & privacy domains, having an extensive background in the technical delivery of Security operations and projects & well-versed with multi-cultural environments with a focus on achieving a secure and sustainable ecosystem. Amit has also contributed to the initiatives by the governments to define the Cyber Security Strategy at the national level and submitted te proposals to define the long-term strategy for securing IoT networks.
Before Nokia, Amit worked with IBM as Leader for Security & Risk Management group for India’s largest telecom operator. He has acclaimed various reputable professional certifications such as Certified Information System Security Professional (CISSP), Project Management Professional (PMP), Information Technology Infrastructure Library (ITIL) and other OEM based certifications



Leave a Reply