A Standard for Home Gateway Security
ETSI’s recently published TS 103 848 is one of a number of standards that ETSI is developing that derive from the security template for Internet of Things devices defined in ETSI EN 303 645. The reason that a standard for the security of Home Gateways is so important is embedded in its title. It protects our homes from the digital thief and burglar in the same way that our front doors protect our homes from the more traditional thief and burglar.
Protecting our home is something we can never be complacent about and the home gateway addresses the digital world and the gateways and windows into our lives that the digital world offers.
Home is often used as a synonym for security – it’s where we feel safe, it’s where we spend our private time, and only rarely do strangers come into our home and never uninvited. The need to be always connected, for work, for social life, for entertainment, for banking, now means that our homes have more and more guests in them and we need to be assured that they are welcome guests that don’t abuse our hospitality. The home gateway is, in many ways, the digital front door to our digital home, and like all our front doors we only want to allow visitors in when we’ve given them permission.
In ETSI the primacy of security in standards for communication has been a driver for a number of years. The growing concern of more and more internet connected devices prompted a number of ETSI members to bring their experience in national guidance and security development together and to develop EN 303 645 to act as a baseline for all IoT devices. The aim at the time was to bring all IoT devices to the market with a level of security that started to take away uncertainty for the buyer and user as to a device offering any security at all. This has been backed up by also standardising the tests for this base level of security in ETSI TS 103 848 Achieving this baseline has been hugely important as it now gives us the opportunity to build higher and deeper defences from a common and testable base. This is where we now sit with the Home Gateway — we are building on the success of EN 303 645, and moving it away from its IoT base into a much more complex environment, to again raise the barrier against the digital thieves and burglars intent on gaining access to our digital homes.
The approach in ETSI to IoT security, and more widely to device and service security, has been to establish a framework and baseline, and to build out from that to both validate it and to extend it for things just outside the baseline. In addition ETSI has been building guidance and examples of the application of the baseline, most recently encouraging a formal template to make it clear where the baseline is extended or, in rare cases, where it doesn’t apply.
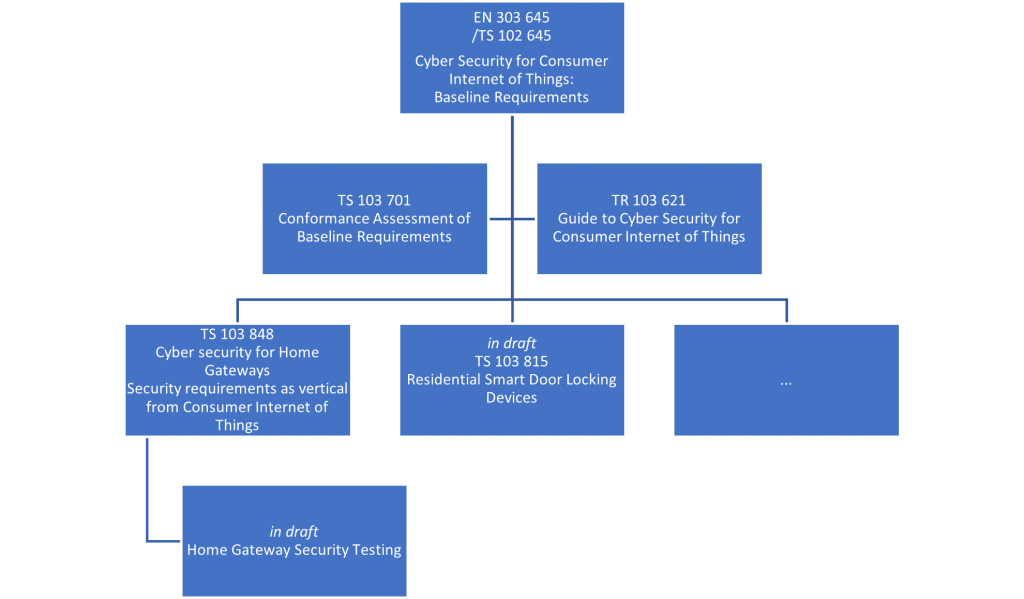
In technical terms the core principles from EN 303 645 remain in place and are simply specialised and selectively strengthened. Thus all the core requirements from the baseline (see below) also apply to the home gateway.
- No universal default passwords – Extended for HG
- Implement a means to manage reports of vulnerabilities
- Keep software updated – Extended for HG
- Securely store sensitive security parameters – Extended for HG
- Communicate securely – Extended for HG
- Minimize exposed attack surfaces – Extended for HG
- Ensure software integrity – Extended for HG
- Ensure that personal data is secure
- Make systems resilient to outages
- Examine system telemetry data – Extended for HG
- Make it easy for users to delete user data
- Make installation and maintenance of devices easy – Extended for HG
- Validate input data
The extension to Home Gateway has to address the biggest diversion from many other IoT devices in that it straddles the home and internet environments. Whilst it’d be easy and naïve to suggest the internet environment is a wild and dangerous place, and home as one of peace and tranquillity, the approach taken isn’t all that far from that characterisation. In common with the generic IoT standard it is assumed that the user doesn’t have any specialist knowledge, and so security should be baked-in, maximised by default, and difficult to remove whilst also being as unobtrusive as possible. Obvious differences from the generic IoT model arising from the 2 faces of the Home Gateway are that the “internet” side is often managed by the service provider and the “home” side by the home administrator. The result is that the requirements from the generic IoT model are added to in order to ensure this key idea of separating the home and internet sides of the device is maintained.
What ETSI has developed with this new Home Gateway security document is important in that it makes it possible to achieve a high level of baseline security at the border of the internet and home. It also strengthens the idea that simple security models developed to be universal can indeed be extended and applied to vertical domains without invalidating the universal model. Furthermore in developing a template and guidance what ETSI’s CYBER group has been able to demonstrate that developing standards are important. During the entire development of the Home Gateway requirements, and continuing in the development of test and validation of the requirements, there has been involvement from all parts of the stakeholder community. This means developers, manufacturers, operators, regulator and testers have all come together to make the common baseline a useful one. Standards here are intended to be challenging and to push to the front of state of the art, and then to lead from the front. The Internet of Things is a good model for this as it forces acknowledgement of the connected world, of complex supply chains, and of complex stakeholder involvement. Its success to date is acknowledgement that standards can make things work securely.
Scott Cadzow
Scott Cadzow, Vice Chair of ETSI Encrypted Traffic Integration Industry Specification Group, participant to ETSI Technical Committee CYBER.

