Hybrid and Multi Cloud Security
This article is the first one in a two-part series covering the complexity and the challenges we face as cybersecurity professionals, in a world where clients are using multiple clouds as well as local infrastructure to run their business. This first article will focus on the various challenges in this environment, with the next one focusing on how we can control the complexity, and thus risks, in hybrid and multi cloud environments.
Cloud is slowly, but surely, becoming a bigger thing for many companies, but only a few of them are moving to the cloud as the primary source of IT services. Many are using the cloud in a hybrid scenario, with some IT on premises and other parts with an external cloud provider. This has been a challenge for many years and is well known about. The new challenge is the ubiquity of cloud vendors and the plethora of various services they supply to their customers.
Most companies utilize multiple different cloud vendors, depending on their needs, and combine these with their on-premises IT systems. A hybrid setup with only one cloud vendor does exist, but the various specialized cloud providers, like the Oracle and SAP, are providing services that originally ran on-premises, adding to the complexity of the hybrid scenarios. Even companies fully in the cloud will have multiple cloud vendors in their setup, to cover all their needs.
One question naturally manifests itself, why are companies/organizations still running their own IT infrastructures? It is a matter of sensitivity of information and associated risk. R&D companies, for instance, will want to keep their research data in house. National regulation is placing restrictions on data storage as well. In Denmark, where I am located, there are governmental regulations that mandates that certain data on danish nationals, and the like, is to be kept within national borders. It is affectionally known as ‘the war rule’ here in Denmark.
As is well known, each vendor has their own way of doing things, sometimes in conflict with other vendors. When integrating cloud solutions from different vendors, like in the figure below, we are presented with challenges that are unique to the hybrid/multi cloud environments.
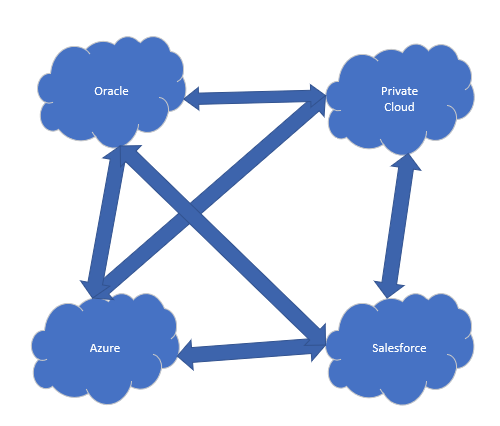
In addition to these challenges, as more cloud vendors are added to fulfill the business needs, we are looking at an almost exponential increase in communication connections between the individual vendors ( ![]() = number of connections). So, aside from having to protect multiple clouds, we have to contend with an almost exponential increase in the number of communications lines we have to protect, since the individual cloud environments will most likely need to communicate with one another.
= number of connections). So, aside from having to protect multiple clouds, we have to contend with an almost exponential increase in the number of communications lines we have to protect, since the individual cloud environments will most likely need to communicate with one another.
For instance, if we have a Salesforce account and an ERP in the Oracle cloud, odds are that the CRM system from Salesforce will needs to write customer data to the ERP system and the ERP system needs to communicate updates to the CRM system. If we add to this heterogenous infrastructure environment a custom application that needs to run on top of the various clouds, then we are looking at scenario like the one below.
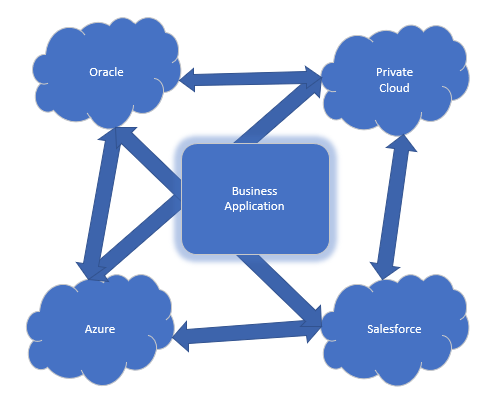
In all likelihood, there will be one or more applications running on multiple clouds – whether or not it will run on top of all of them at the same time, as pictured above, is another question. The main point is, when we are adding cloud vendors to an infrastructure, we are also adding risks and increased complexity that must be handled in our approach to securing organizations.
In the coming years, we will see a vast increase in the utilization of multiple clouds in organizations around the world. As the cloud matures, and organizations increasingly focus on their core business, and less on running the supporting infrastructure, various cloud vendors will step up to provide the IT services required. This creates an almost self-reinforcing loop as the services provided will become increasingly specialized and usable for a wider range of cloud customers.
This was the first article in the series, focusing on the challenges we are facing with the use of hybrid and multiple clouds. The next article will provide advice and pointers on how to mitigate associated risks and secure such an infrastructure.
Tom Madsen
Tom Madsen has been active in the cybersecurity industry for more than 20 years. Tom graduated from the University of Aalborg and covered several technical roles in security during his professional career. He is certified as CISSP, CISA, CISM, CGEIT, CRISK, CCSP, CDSPE and CSSLP, and has published the book "The Art of War for Cybersecurity". He is currently writing a book 'Security Architecture - How & Why'.


Pingback: Cloud Security Governance - Cybersecurity Magazine