Hybrid & Multi Cloud Security – Greater Control of the Risks
This is the second article, in a series of two, dealing with the security challenges introduced with hybrid and multi cloud implementations. The first article focused on the concrete challenges that are introduced with hybrid and multi cloud. This second article focusses on how we can mitigate some of the risks and reduce the complexity that are typical of hybrid and multi cloud implementations.
First off, let us look at the second figure from the first article, just to get back in the thick of it.
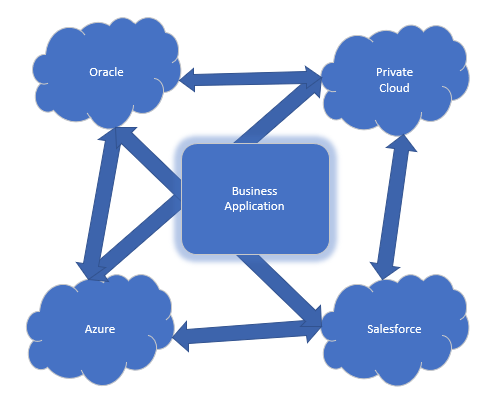
Please do not get caught up on the specific examples of cloud providers in the figure. These could have been any of the vendor out there. So, we know of the challenges that having multiple cloud vendors introduce into our risk profile and cybersecurity. How do we go about addressing these?
How-to
The points that are following are some of the things that will have to be considered as part of the protection of hybrid and multi cloud scenarios.
User Accounts
Each cloud vendor has their own way of authenticating the users of the cloud. The first thing we must consider, is how to streamline and consolidate the user accounts that are used in the hybrid/multi cloud infrastructure. This can be a significant challenge, depending on the cloud vendors, but having a common authentication method across the clouds will go a long way in decreasing the complexity and thus the risk involved.
Align the Tooling
As much as possible, use the same tools across the various clouds in use. Tools in this context are the security tools you are using in the infrastructure, like Intrusion Detection and Prevention Systems (IDS/IPS), firewalls, anti-virus tools, and the like. This will make the protections and monitoring of the cloud environments much easier for the staff tasked with that. Giving them multiple different tools for each of the vendors will make their job much more difficult and increase the risk that something is not monitored in one of the clouds or is missed because the staff cannot be equally familiar with all the tools in use.
Common Networking
This one can be a significant hurdle, but it relates to the point above on the tooling in use. Harmonizing the network policy and the network implementation across the vendors and on-premises will make the monitoring easier and the maintenance far less challenging. With networking in this context, this refers to common routing protocols, common communication protocols (IP, IPv6), common management protocol and standardized VPN connections between the cloud and the on-premises equipment.
Monitor for Change
Change in this context is change in the offerings from the cloud vendors. Microsoft for instance is rolling new code onto Azure every three weeks, making it a rapidly changing cloud offering and something that Azure customers and consultants are struggling to keep up with. A rapidly changing cloud environment might sound like a risk, but most often these changes provide us with additional functionality or increased security for the workloads we have with the cloud vendors. That is a good thing, but we must have a process in place where we are continually keeping track of these changes and make informed decisions on how implement, or ignore, these changes.
Governance and Policy
Governance is one of my personal go-to tools for increasing the maturity and cybersecurity. Governance becomes especially important in complex environments, like hybrid and multi cloud implementations since these cases will introduce complexity into the overall infrastructure. Having governance in place makes this complexity easier to handle and can help with keep it under the control of the customer. Complex infrastructures are a hacker’s friend, since these kinds of infrastructures often have holes and weaknesses that have slipped through the cracks while the infrastructure is implemented.
Systems Development
As mentioned in the previous article, frequently customers will have their own applications and tools running on top of the various cloud vendors, often using features from multiple different vendors at the same time. Application security has been on top of our agendas since the 90’s, but with the introduction of the cloud and the hybrid/multi cloud case, it is only becoming more and more important. An application running on multiple clouds has the potential to compromise each of these clouds, along with the applications running on them. So, when developing applications, we absolutely must develop in a secure manner and use the tools that the cloud vendors provide to secure applications. These tools differ from vendor to vendor and are prone to change over time, making the governance and monitoring mentioned earlier an important tool in this context as well.
Summary
This all makes the hybrid/multi cloud scenario look like something to be avoided, but with the right approach and keeping security in mind, there is nothing to prevent you from utilizing multiple cloud vendors and integrate these with the on-premises infrastructure. As security professionals, it is our job to provide good information and advice on how to create this integration in a secure manner and monitor and maintain this security as part of the infrastructure. A complex job, make no mistake here, but the cloud will only increase in importance in the coming years, making the points made above more and more important.
As I see it, the hybrid/multi cloud environment will become the new normal as time goes by, making our jobs more challenging, but also much more entertaining, since we will have to deal with a plethora of different scenarios and business cases involving hybrid and multi cloud implementations.
Tom Madsen
Tom Madsen has been active in the cybersecurity industry for more than 20 years. Tom graduated from the University of Aalborg and covered several technical roles in security during his professional career. He is certified as CISSP, CISA, CISM, CGEIT, CRISK, CCSP, CDSPE and CSSLP, and has published the book "The Art of War for Cybersecurity". He is currently writing a book 'Security Architecture - How & Why'.

