Security Basics: Security Services and Solutions
Security Services
There are five major security goals that are also known as security services and can also be used as security requirements. These goals are discussed as follows.
- Confidentiality: This is for the protection of the data from disclosure to an unauthorized person. Encryption is used to fulfill this goal. With an active attack it is possible to decrypt any form of encrypted data (given there is a good mathematician/cryptographer or a person with a powerful computer and no time limit); thus confidentiality is primarily considered a protection against passive attacks.
- Authentication: The authentication service is concerned with assuring that a communication is authentic. In the case of a single message, such as a warning or alarm signal, the function of the authentication service is to assure the recipient that the message is from the source that it claims to be from. In the case of an ongoing interaction, such as the connection of a terminal to a host, two aspects are involved. First, at the time of connection initiation, the service assures that the two entities are authentic (i.e., each is the entity that it claims to be). Second, the service must assure that the connection is not interfered with in such a way that a third party can masquerade as one of the two legitimate parties for the purposes of unauthorized transmission or reception.
- Access control: Access control is the ability to limit and control access to the systems, the networks, and the applications. Thus unauthorized users are kept out. Although given separately user authentication is often combined with access control purposes; this is done because a user must be first authenticated by, for example, the given server and the network so as to determine the user access rights. Implicitly access control also means authorization.
- Integrity: Prevents unauthorized changes to the data. Only authorized parties are able to modify the data. Modification includes changing status, deleting, creating, and delaying or replaying of the transmitted messages.
- Non-repudiation: Neither the originator nor the receiver of the communication should be able to deny the communication and content of the message later. Thus, when a message is sent, the receiver can prove that the message was in fact sent by the alleged sender. Similarly, when a message is received, the sender can prove that the message was in fact received by the alleged receiver.
Besides the above mentioned security requirements there are some general requirements that play an important role in developing the security solutions; these are the following:
Manageability: The load of the administrator must not be unnecessarily increased by adding security, while the deployed solutions should be easy to manage and operate in the long term.
Scalability: A system must be scalable, which requires the security scheme deployed in the system to be equally scalable while maintaining the level of security. Here the term scalability is being used in its broadest sense, scalable in terms of the number of users and in terms of an increase in system size (i.e., addition or extension of new system elements).
Implementability: A simple and easy way to implement a scheme is extremely important. Thus a security scheme must be devised so that it is easy to implement and still fulfills the security requirements.
Performance: Security features must have minimum impact on the network performance. This is especially important for real-time communication where the security requirements must be met while the required quality of service is met. Performance also goes hand in hand with the resource usage of the medium; the security solutions must not, for example, cause a decrease in the overall capacity of the network.
Availability: This goal is closure to the five goals mentioned earlier in the section. Any service or network should be available to the user. Several attacks are possible to disrupt the availability, DoS being the major one.
Common Security Solutions
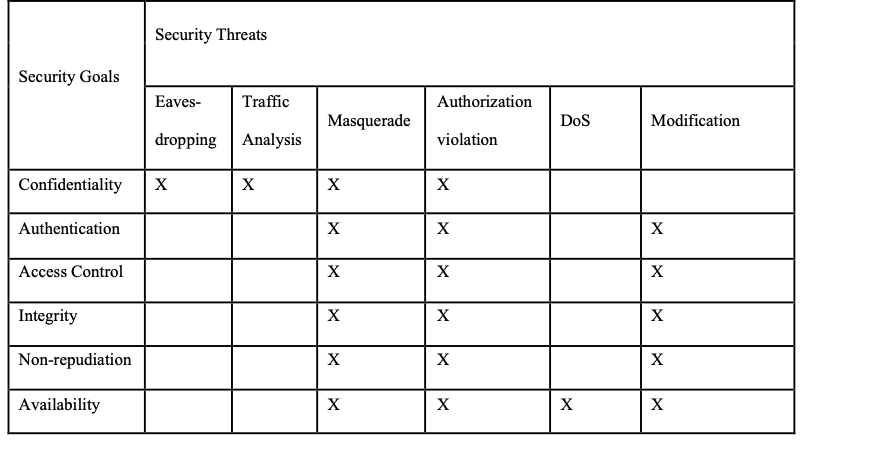
In this section the security threats are mapped to the security goals. Knowing which threat can be countered by which goal, the next step is to find the security solutions or mechanisms that can fulfill the security goals. A mapping of security threats and goals is given in Table 1, where X in a cell represents that the given security goal can counter the given threat. It should be noted that a security goal can fail to counter a threat sometimes.
Table 1
Mapping of the Security Threats to the Security Goals
In wireless systems one of course has to observe that the communication takes place on a medium that is accessible to all. On the other hand IP based communications basic issue is that IP is well understood by many and the Internet has provided access to tools that can be used even by a novice to successfully perform attacks.
Anand R. Prasad
Dr. Anand R. Prasad is a global leader and expert in information and cyber security who has delivered security solutions for 5G, 4G, virtualization, SOC, Wi-Fi, mobile devices, enterprise and built GRC processes from scratch.
Anand is Founder and CEO of wenovator LLC, a global provider of cybersecurity services and consulting with top-tier clients right across the telecommunications industry. Dr. Prasad is also a Senior Security Advisor of NTT DOCOMO, providing advise on all aspects of cybersecurity for the company, Advisor to CTIF and Advisory to GuardRails. Prior to which he was Chief Information Security Officer of Rakuten Mobile, the world's leading MNO with the very first cloud-native 4G / 5G network implementation. As CISO of Rakuten Mobile Anand led all aspects of enterprise and mobile network security from design, deployment to operations.
With over 20 years of experience, Anand has also held key roles in NEC, Genista, Lucent Technologies and Uniden. He is an innovator with over 50 patents, a recognized keynote speaker (RSA, GWS, MWC, ICT etc.) and a prolific writer with 6 books and over 50 peer reviewed publications. Anand was the Chairman of 3GPP SA3 where he led the standardization of 5G security. He did his ir (MScEE) and PhD from Delft University of Technology, The Netherlands. He is a Fellow of IET, Fellow of IETE and CISSP. Anand is Editor-in-Chief of the Journal of ICT Standardization and Co-Founder & Co-Editor of Cybersecurity Magazine.

