What’s Roaming Your Network?
A surge in consumer traffic powered by the increased use of internet-based digital content and enhanced mobile broadband services for mobile devices has led to exponential growth in global roaming traffic in recent years. All this plus the proliferation of the internet of things (IoT) will lead to even greater use of roaming services.
In the past, mobile network operators (MNOs) held roaming agreements with a few selected, trusted partners. Today, because of emerging use cases and inflation in roaming traffic witnessed in the last couple of years, MNOs are opening up their networks to a large number of roaming partners, services and other operators. Adding to that, roaming IoT services are expected to bring in 20-30% of operator revenues by 2020, with average data traffic between network-to-network roaming partners in mobile networks expected to exceed 1GB per subscriber. This will increase the need for MNOs to open up to third-party services even more.
This exposure to different third-party services, coupled with uncontrolled and unmanaged data and subscriber traffic exchanges with partner networks, has led to increased security risks that threaten the availability of network infrastructure while impacting revenue opportunities for MNOs from the roaming user base. The surge in roaming has greatly widened the threat landscape and made roaming networks complex and difficult to secure. In summary, three main challenges are creating a perfect storm of roaming network security risks.
- Threat Visibility & Control
a. Challenge: Lack of visibility into threats from inter-operator networks outside the operator’s control
b. Impact: Overwhelms the network infrastructure with adverse effects on subscriber experience and services
- Services Exposure
a. Challenge: Infrastructure services are exposed to partners, other operators and services
b. Impact: Causes network congestion and significantly impairs network and services
- Unknown Threats
a. Challenge: Increased attack surface with new vulnerabilities and exploits that are not yet understood
b. Impact: Difficulty in keeping up with unknown threats infiltrating the network
A primer on mobility protocols used in GRX/IPX Networks:
Mobile network protocols (serving control, signaling and user planes) are critical to establishing and maintaining network operations. GPRS Tunneling Protocol (GTP) is, in effect an IP based tunneling protocol that allows mobile subscribers to maintain a data connection for internet access while on the move. It has many different variants such as, GTP-C, GTP-U and GTP’. While the protocol variant, GTP-C (GTP control plane), serves on the control plane carrying control and signaling traffic, GTP-U (GTP user plane) on the other hand, serves on the user plane carrying network user traffic. The GTP’ protocol is used to transfer charging data to the Charging Gateway Function.
Apart from GTP, core signaling protocols such as Signaling System No 7 (SS7) and Diameter uses Stream Control Transmission Protocol (SCTP) as the IP transport-layer protocol to carry signaling traffic on various interfaces. These protocols typically perform billing, traffic/subscriber mobility management, and quality of service (QoS) policy management, among many other functions. The signaling protocol evolution started with SS7 in 3G networks, then progressed to “Diameter” in 4G. Now signaling is carried over HTTP/2 in emerging 5G networks.
Evolving Threat Landscape
As networks evolve, so does the threat landscape. Vulnerabilities and security weaknesses in these control and signaling protocols have been studied and analyzed by industry standardization bodies, such as ENISA and GSMA. Let’s now look at the attack landscape on roaming networks in detail.
Signaling attacks have been on the rise across 4G and 5G networks. An attack on the signaling and control plane traffic exploits vulnerabilities on GTP-C and SS7/Diameter over SCTP in many different ways. This results in signaling storms that unleash Denial of Service (DoS) attacks on critical network elements, causing service disruption. Other attacks on roaming networks include various fraudulent activities, subscriber overbilling, and even illegitimate disclosure of sensitive information about the network and its subscribers, causing massive data breaches and loss of subscriber privacy. Based on a recent service provider security survey, the results of which led us to conclude that signaling attacks in 2018 have risen 2.5 times more than what we saw in 2014. Also, looking into the future, we noted that 88% of the respondents agree that signaling security between inter-operator roaming networks will be crucial to implementing 5G.
The attacks on roaming networks not only target the signaling plane but also lead to a widening of the attack surface from which known and unknown threats infiltrate the data plane. Operators can combat growing threats on their roaming infrastructure by leveraging deep visibility and comprehensive GTP security on their roaming interfaces.
Mobile network operators should use the following best practices to help navigate risks and secure their roaming networks, while enabling a seamless roaming experience for subscribers:
Three Best practices to Securing Roaming Networks
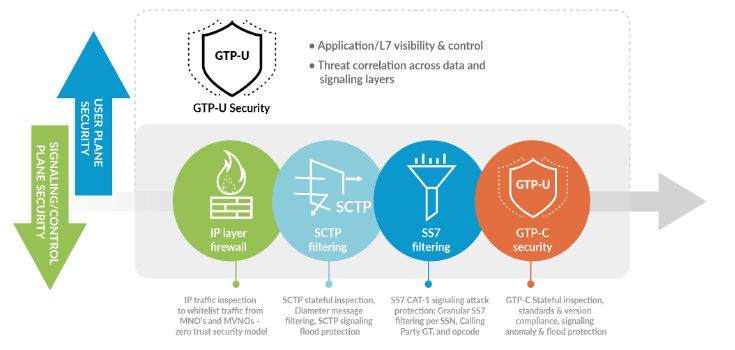
- Adopt a Zero Trust Security Model
Adopt a least-privileged access strategy and strictly enforce access control by whitelisting traffic only from trusted MNO’s or MVNO’s. For example, to allow only legitimate application interactions between the mobile network entities.
- Reduce the Signaling Attack Surface
Enhance the security posture by deploying a preventive approach to security, by implementing critical security controls on GTP-C, SCTP, SS7 & Diameter protocols
- Perform GTP-C stateful inspection, standards and version compliance, signaling anomaly and flood protection.
- Improve SCTP/SS7/Diameter security by implementing SCTP stateful inspection, Diameter message filtering and flood protection, granular SS7 filtering for CAT-1 signaling attacks, etc.
- Complete Visibility and Control with User Plane Inspection
Remember that secure access is not enough; constant inspection and prevention must be included to successfully weed out the threats and secure your network.
- Enforce complete visibility of GTP-U traffic to proactively identify and block malware, C2 and unknown threats.
- Accelerate security investigations by coupling GTP-C stateful inspection with GTP-U content inspection to automate threat correlation of IMSI (subscriber identity) and IMEI (device identity) to threats.
A next-generation security platform that adopts a preventive approach to security can stop the majority of real-world attacks to build a resilient network with robust security mechanisms in place. Establishing application-layer visibility and consistent security all locations across the mobile network is essential to providing future-proof security.
Lakshmi Ananderi Kandadai
Results-driven technology leader and enterprise visionary combining outstanding technical & marketing talents, with proven track record of creating innovative go-to-market strategies including conceptualizing, launching and positioning IP (Cloud, SDN/NFV) & RAN mobile-edge technology products and solutions in a fast paced business environment.
Designing and integrating end-to-end network solutions based on products and solutions from IP & Broadband, with focus on developing value proposition for the company's IP Portfolio.
Evangelized solutions through presentations and discussions with C-level customers, internal and external stakeholders and global events.

